With integrated Next Generation Firewall Features Firepower is extremely effective at blocking external threats. But, are you exploiting all the knowledge and information Firepower has about your network?
In this blog post we will focus on how you can build your Cisco Firepower Management Center and get an overview of devices in your network that are infected with malware – and are being used in botnet or similar.
Firepower Management Center works out of the box with Default Dashboards on the front page. By adding on just a few improvements to the dashboard you can use the implementation of Firepower far better and get a lot more out of the data that Firepower gathers in the network.
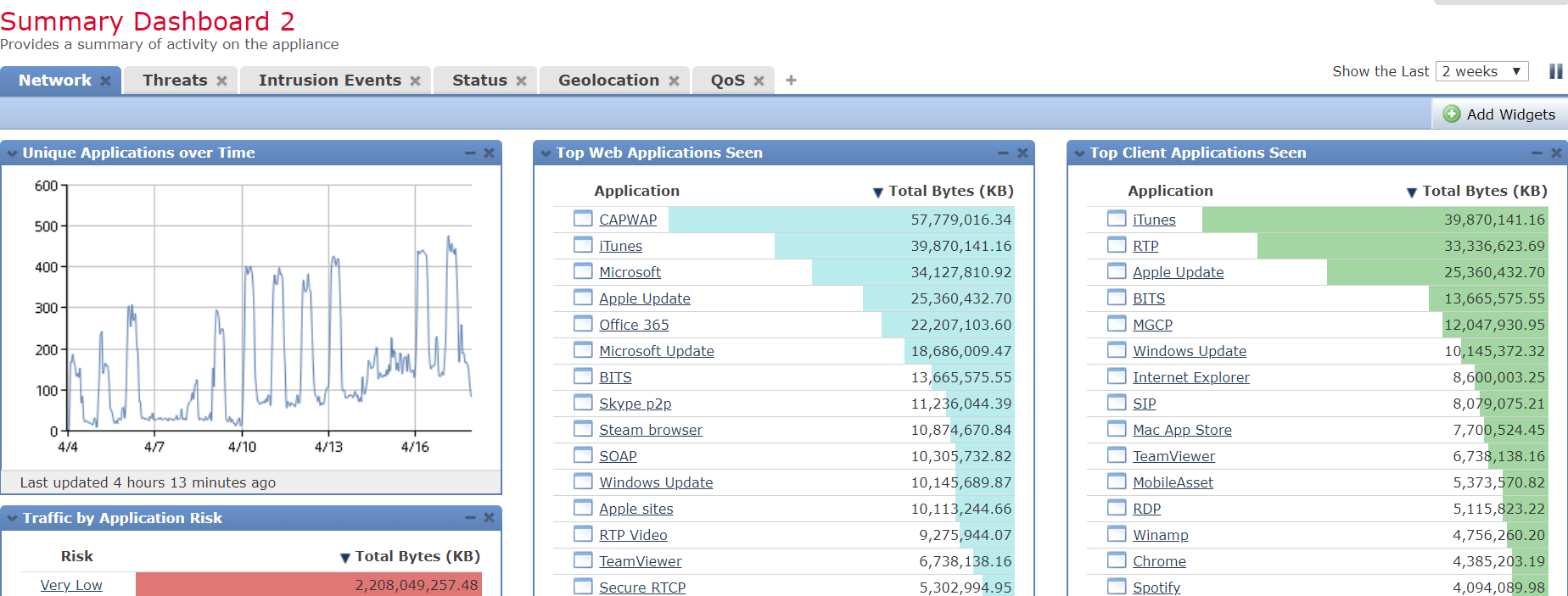
Firepower can of course block connections to known threats, but often there is a reason why the connection is being created in the first place.
Identify the threat
It is not enough to block the connection – we must naturally find the cause of the problem in the device.
Is the device infected with malware? Is the device part of a botnet that was not active when the connection was blocked by Firepower?
If so, it is the primary goal of IT to find these devices and get them cleaned. If AMP for endpoints is implemented it is relatively simple to block and remove these infections. If the company has not invested in AMP for endpoints, we can use Security Intelligence from Firepower Management Center to find the devices and clean them.
In most networks there are devices that fall outside the administrative rights of the IT department. These could be employees own smartphones or other IoT devices under the BYOD umbrella (Bring Your
Own Device). We, therefore, have the task of limiting access from these devices to internal resources, to prevent infections from spreading.
But what about all the devices under the IT department’s domain? These must be shown in the light of Firepower Management Center so that we can react to internal security incidents.
Cisco gathers intelligence in Firepower from across Intrusion Prevention, Advanced Malware Protection, URL filtering and Security intelligence. It is then presented as Indicators of Compromise or IOCs.
Indicators of Compromise is activated when Firepower has confirmed that a device is infected or has sent traffic to IP addresses or URLs that are known to be insecure and full of baddies.
Indicators of Compromise in Firepower Management Center
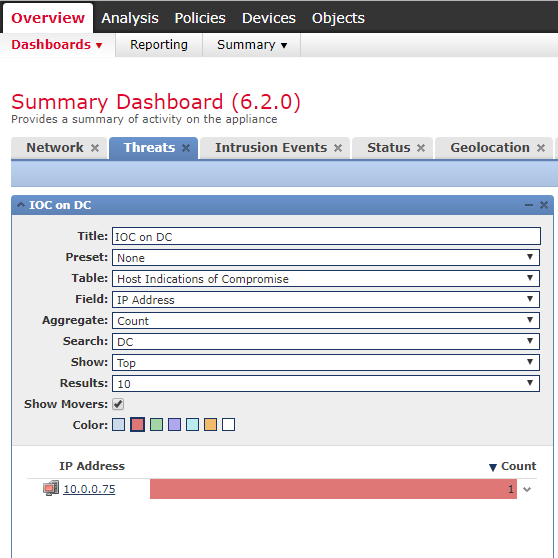
To find Indicators of Compromise in Firepower Management Center, we can open Summary Dashboard –> Threats as shown below.
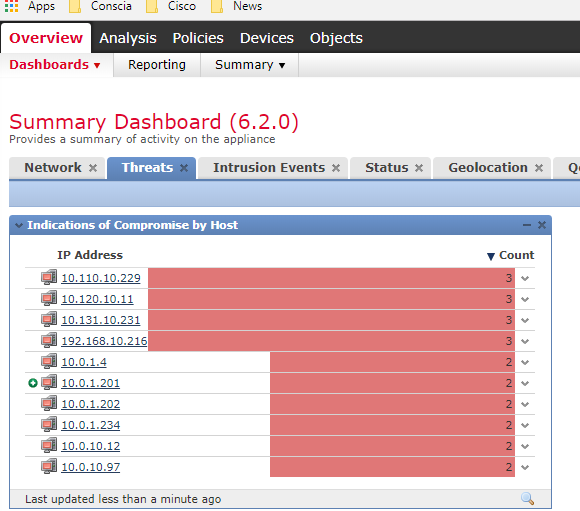
On this dashboard we can see a Widget called Indications of Compromise by Host. This dashboard looks at the entire network, which means that you get IOCs on all network devices that contain employees’ mobile devices and all other potential devices outside the administrative domain of IT.
Cisco has fortunately made it possible to create several different Widgets, where we can specify which IP addresses must be included in each Widget. So, we will create a new Widget that contains only units under IT’s administrative domain such as servers and PCs in the IT department’s Active Directory Domain.
To create this new Widget, you start by creating a Search as follows below. Analysis –> Search
In Search you choose Host Indications of Compromise to the left – marked in red – then you define which network the Search must contain under IP Address – marked in blue.
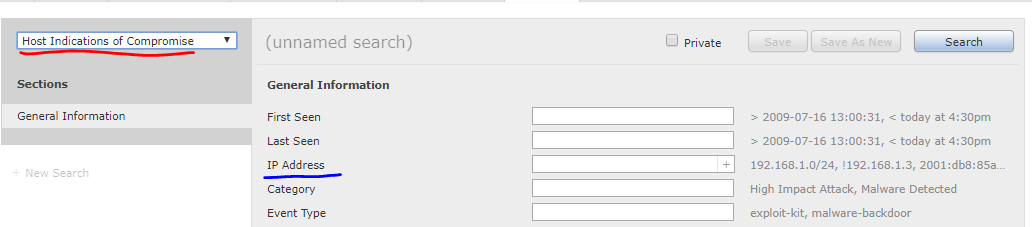
Then select Save as New and give a name– for example DC.
Now create a new Widget on your Dashboard. Click Overview –> Dashboard, select your Dashboard, and then click on Add Widgets in the right corner.
The different Widgets will then be presented in Firepower Management Center. In this case, select Custom Analysis as follows:
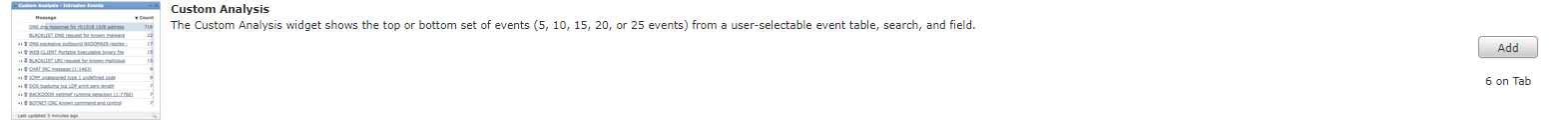
When you click Add the new Widget will be added to your Dashboard, you can then return to Overview –> Dashboards to configure the newly added Widget.
In the above Widget I have configured Host Indications of Compromise and the previously created search. Therefore, it only shows the IOCs that Firepower Management Center has seen in the network specified in the search.
It is also possible to create a Widget with User Indications of Compromise, which makes it simpler to identify the individual PC or user.
Then you can select from the list’s interesting IOCs. In the example above there is only one individual PC, IOC.
By clicking on a specific device marked as Indicator of Compromise on our Widget, Firepower Management Center will display a tab with the IOCs found on that specific device.
When you click on Hosts even more information is displayed, including, the specific IP.
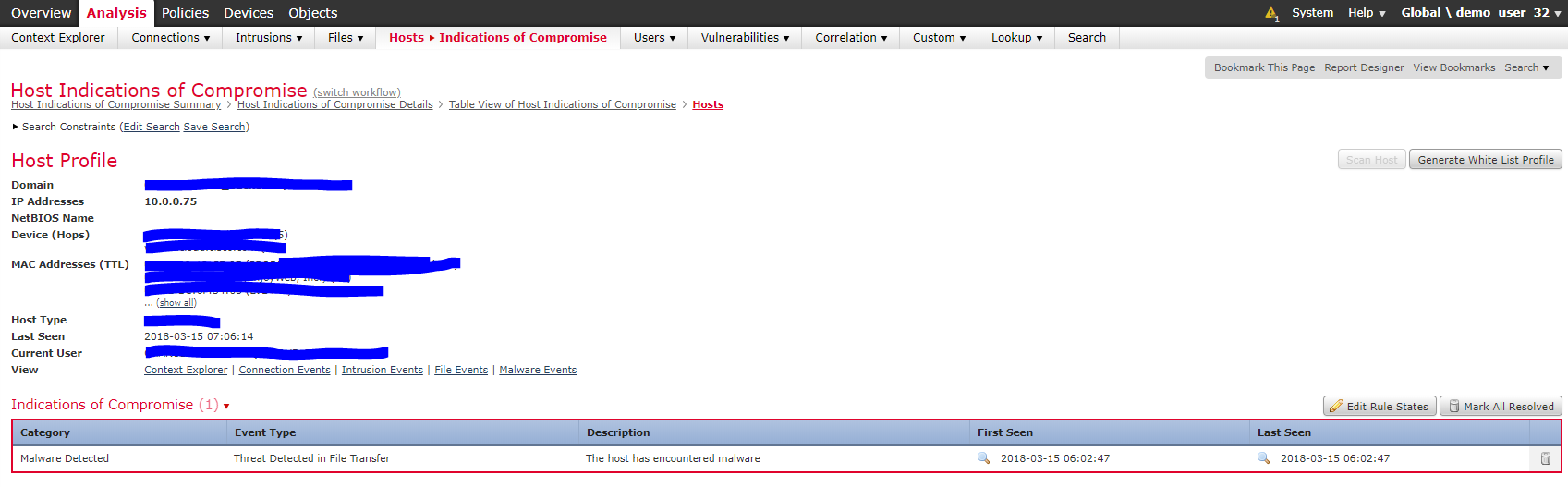
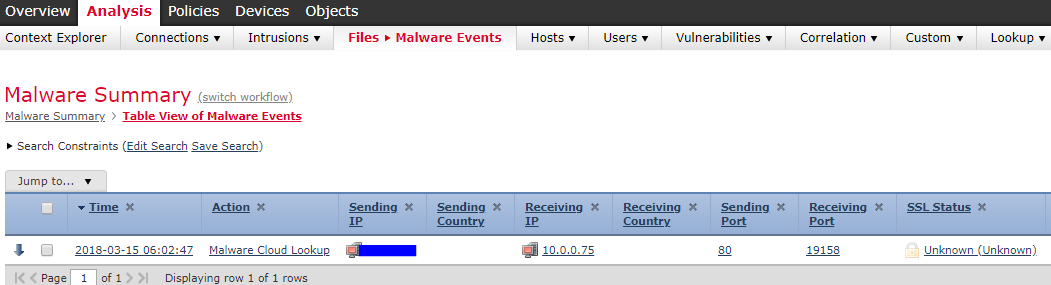
As shown, this device has sent or received malware in a file transfer. Select the little magnifying glass as shown below to get more information on the destination and frequency of the incident.
A log can also be displayed with source and destination IP addresses. See the example below.
When an infected server and/or PC is identified our work starts with getting to the cause of the infection – as well as finding a solution to the problem.
The threat is often blocked by Firepower, but the device behind the IP address could also be infected with other malware. If a laptop is infected with malware, there is great risk that the malware will spread to other networks when the employee, for example, takes his laptop to other locations and networks.
That is why it is necessary to scan the relevant laptop with an Endpoint Protection Solution – for example, AMP for endpoints – or ultimately reinstall the machine to remove the threat.
The threat is identified and removed
Once we have identified the cause of the IOC, cleaned and removed the threat, the IOC must be marked as Resolved on the Host page. You can also do this by clicking directly on the IOC in our search, as shown below.
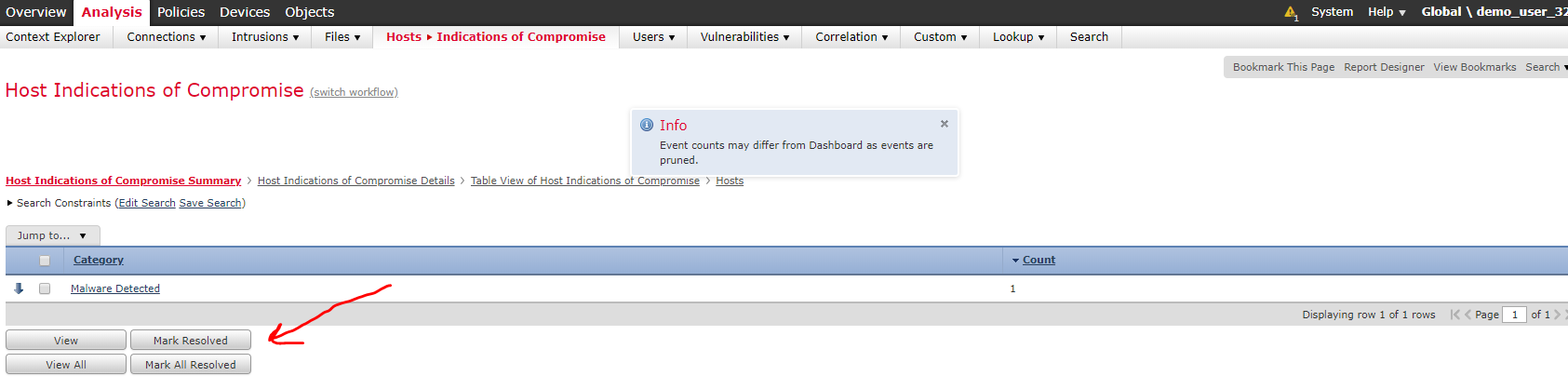
The IOC in question will then be removed from Firepower Management Center, which makes it easier to get an overview of remaining and future IOCs.
My clear recommendation is to go through the list of IOCs on the Dashboard weekly, to ensure that we continuously keep track of security incidents in the network.
Please get in touch with Conscia to talk about Firepower Next Generation Firewall and Firepower Management Center and all the benefits they have for your business.
Jesper Erbs is a CCIE-certified network expert with a security focus.
He has in-depth insight and significant experience in structuring networks and solutions for network security that give optimal value to the business and increases the security of the network.