Blog
CIS Controls version 8
Center for Internet Security (CIS) has recently updated the CIS controls (May 2021) and we no longer have 20 controls as in CIS version 7.1 but “only” 18 controls. You can find the new version here: https://www.cisecurity.org/controls/v8/ In my opinion the controls have been updated to reflect a more modern approach to cybersecurity. It is not […]

Center for Internet Security (CIS) has recently updated the CIS controls (May 2021) and we no longer have 20 controls as in CIS version 7.1 but “only” 18 controls.
You can find the new version here: https://www.cisecurity.org/controls/v8/
In my opinion the controls have been updated to reflect a more modern approach to cybersecurity. It is not revolutionary changes and as stated by CIS you can still use version 7 but should consider upgrading to version 8 when possible.
CIS has created a picture depicting the changes which I find great in understanding the changes.
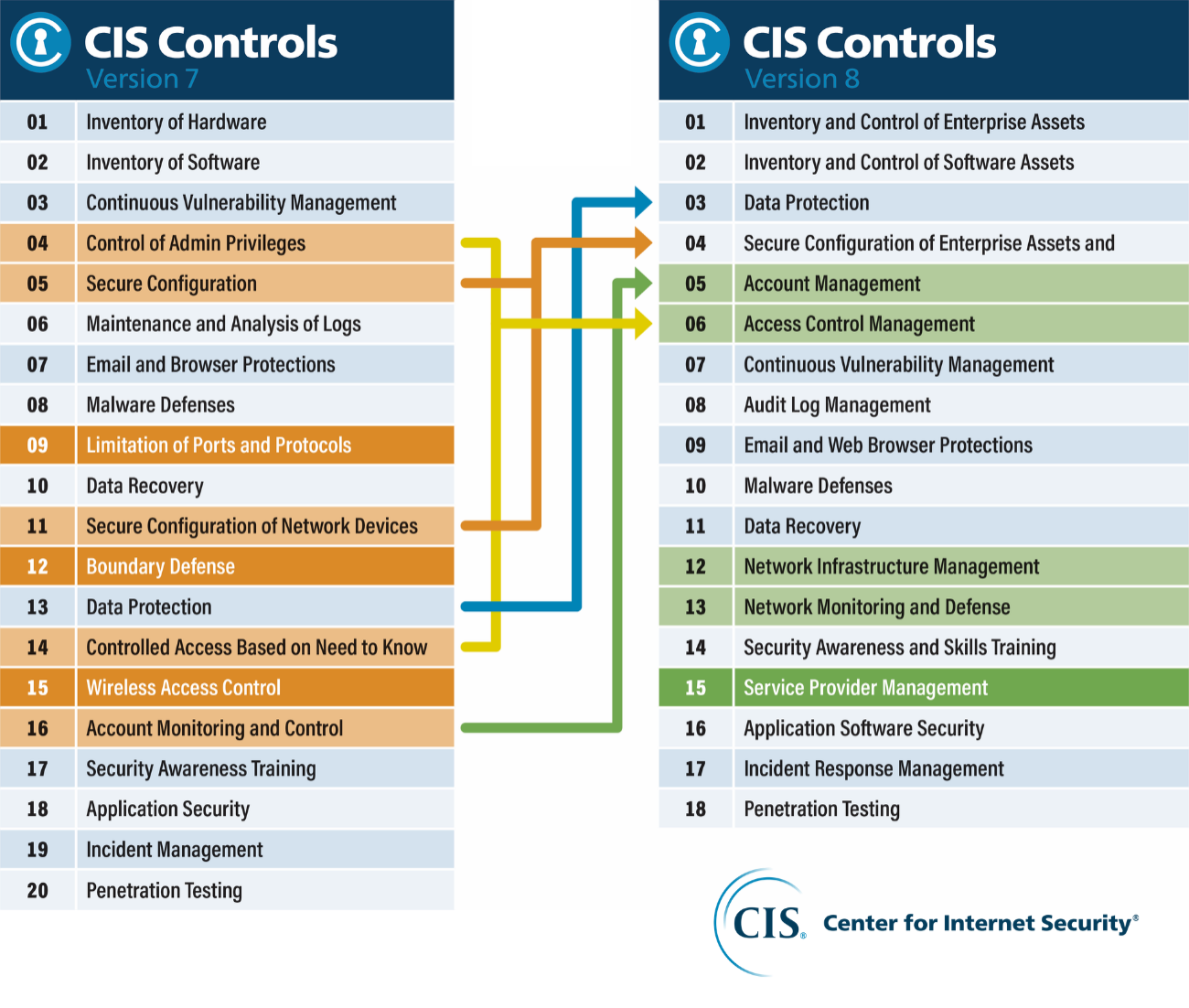
As can be seen from the above some of the controls have been merged – like control 4 (control of admin privileges) and control 14 (controlled access based on need to know) into the new control 6 (access control management). Also, some of the controls have been deprecated like control 15 (wireless access control) and new controls have emerged like control 15 (service provider management).
Gone are also the “basic controls” which used to be control 1-6 and instead CIS has chosen to designate Implementation Group 1 (IG1) as the basic cyber hygiene controls which should be applied to all organizations. IG1 contains almost all of the 18 controls (13, 16 and 18 are not included) which I find quite positive. Although I would have liked to have included some parts of the sub controls (now called safeguards) in control 13 (Network monitoring and defense). Control 8 (Audit log management) does still require log management.
Implementation Group 1 (IG1) is the small to medium-sized organizations with low sensitivity to data most likely employee and financial information. IG2 often stores sensitive client and enterprise information where a major concern is loss of public confidence if a breach occurs.
In my opinion most of the smaller organizations in Europe will fall into the Implementation Group 1 but as soon as they have sensitive information above employee and financial information, they will fall into Implementation Group 2 and thereby increase the number of required safeguards.
You cannot be CIS compliant or be certified after CIS. You can only state that you are following the principles/best practices in the CIS controls, and I really like that.
Another great update is that the CIS controls and safeguards now reflect the NIST Cyber Security Framework (NIST CSF) and I really appreciate the NIST CSF framework for a lot of reasons – mostly because it is freely available compared to the ISO 27000 standard, but also because it provides a more holistic view of the controls in different categories, illustrated below.
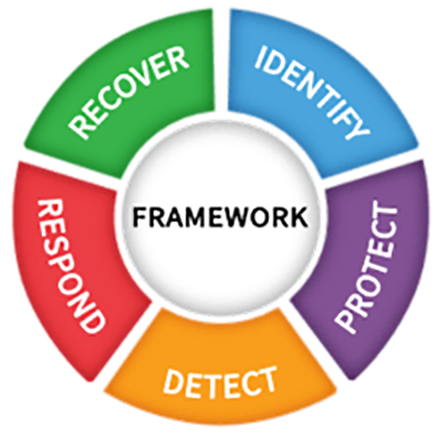
The phases from Identify, Protect, Detect, Respond and Recover shows the completeness and breadth of cybersecurity and where you should have your controls. CIS on the other hands gives you a tool to prioritize your controls and what controls are needed. It does not make sense to have all your controls in the Protect phase and no controls in the Detect and Repond phases. And that is what I often see – customers buying new protection technology like firewalls and traditional AV instead of investing in detection capabilities and EDR software.
If you haven’t read the new CIS version 8 control framework, I can highly recommend it and if you would like to talk to a consultant about how you can implement CIS then please reach out.
Related










