Blog
Cisco Security 2023 – The Year in Review
I hope you have landed well in the new year without any major technical fires that needed extinguishing over the holiday period. For Cisco Security 2023 was filled with exciting news Among other things, they announced their strong bid for a Security Service Edge (SSE) solution – Cisco Secure Access. I have had the opportunity […]

I hope you have landed well in the new year without any major technical fires that needed extinguishing over the holiday period.
For Cisco Security 2023 was filled with exciting news
Among other things, they announced their strong bid for a Security Service Edge (SSE) solution – Cisco Secure Access. I have had the opportunity to look at the solution myself, and I am convinced that we will see much more of Cisco Secure Access in 2024.
Cisco Secure Firewall 4200 series
This was also the year when we were introduced to the Cisco Secure Firewall 4200 series, which is positioned between the 4100 and 9300 series and thus primarily addresses larger enterprise data centers or service providers. Currently, the 4200 series is also one of the strongest, if not the strongest, 1U firewall on the market.
Full focus on Firewall Threat Defense
At the same time, Firewall Threat Defense received a new focus from the development side at Cisco – this time with a great effort to make the platform more stable. It is no secret that most who have worked with FTD in recent years have been able to experience challenges with the software. 2023 was the year when Cisco put their full focus on this problem, and major efforts were launched on their part to stabilize the software. This journey started with the release of version 7.2.4, and the improvements in the 7.2.x train are also continuously integrated into the newer trains (e.g., 7.4.x).
Full control across cloud providers
Cisco Multicloud Defense was also announced based on their acquisition of Valtix. In larger organizations, it is not unlikely that several cloud providers are used, whether it is AWS, Azure, GCP, or OCI. It can be difficult and overwhelming to control rules and traffic across these. Multicloud Defense offers the opportunity to create policies, enforcement, and logging in one policy across cloud providers. This also includes the ability to inspect traffic through IDS/IPS, decrypt, proxy, FQDN, etc.
AI-First for Cisco Security in 2023
Artificial intelligence or AI also became a big buzzword, even non-technically minded people became familiar with this – ChatGPT was even “Word of the Year 2023” in Denmark. Of course, this has not gone unnoticed by Cisco, which also means that we will see much more of “AI-First” in the new year, and I have already had the opportunity to meet Cisco’s AI Assistant through Cisco Secure Access, which can be used to add rules based on basic prompts. Over the year, we will also see this become an integrated part of more Cisco products, including CDO/cdFMC with the possibility for troubleshooting, policy optimization, and more.
Splunk became part of Cisco Security 2023
Of course, we must not forget the “small” acquisition of Splunk, for the staggering amount of 28 billion dollars, which is Cisco’s most expensive and largest acquisition ever. No official announcements have been made about what this means for current Cisco products, or future ones. But we will probably see even closer integrations between Splunk and Cisco products, and not least improvements to products that use logging of one kind or another.
This is just a small selection of the most significant and exciting things, as I see it. There is no doubt that Cisco is making a big push on their Cisco Security in 2023 and the coming years.
Cisco Secure Access
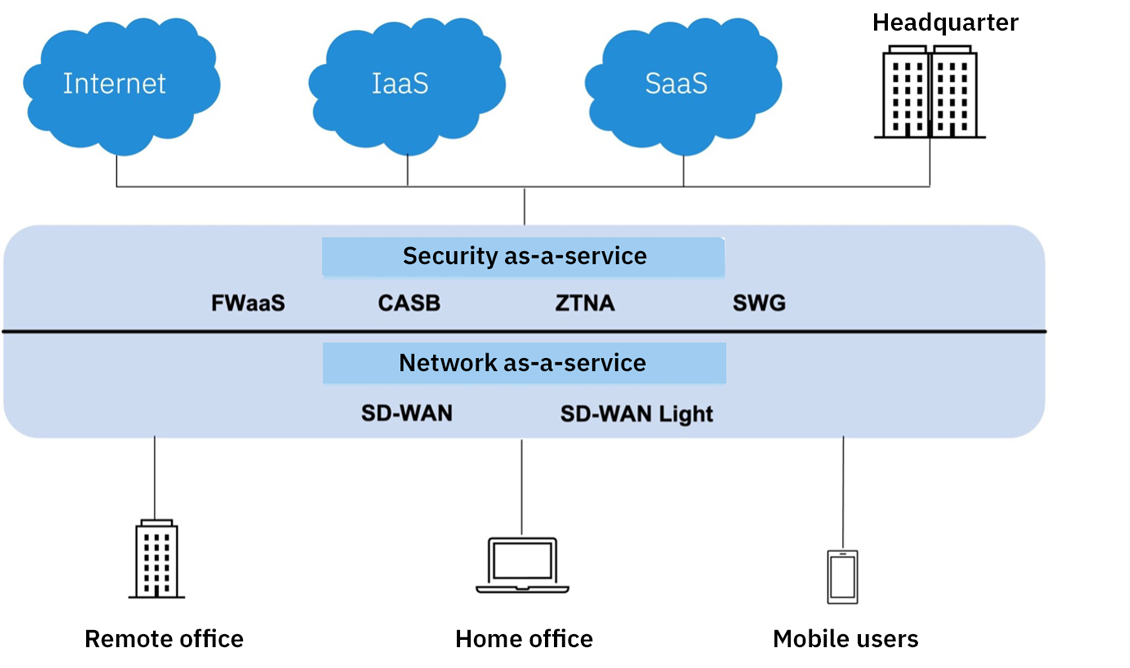 As previously described, Secure Access is Cisco’s answer to a SASE/SSE solution which was announced at Cisco Live 2023 in Vegas.
As previously described, Secure Access is Cisco’s answer to a SASE/SSE solution which was announced at Cisco Live 2023 in Vegas.
I have had the opportunity to test and experiment with this product in recent months. It is still a product that is under massive development, but it is quite clear to me that we are looking at a product that will be very exciting to follow here in 2024.
Secure Access brings most of the good Cisco Secure products to one large combined solution in the cloud. In addition, Cisco’s answer to ZTNA (Zero Trust Network Access) is introduced, both with and without agents on devices, and of course with a Zero Trust mindset behind.
It is a solution that is divided into a Secure Internet Access and Secure Private Resource solution – or a combination of both. In addition, it includes, among other things, FWaaS and VPNaaS globally with the possibility to connect to the closest PoP for the best user experience.
Secure Internet Access uses many of the technologies we know from Umbrella SIG, aimed at traffic flowing from the office, home work, or 3rd party towards the internet.
Secure Private Resource
Secure Private Resource rethinks the Cisco way in which users should connect to VPN to access resources in the data center or cloud. Through the ZTA module in Secure Client, it is possible to access resources without having to connect and authenticate to a VPN client first – this is even possible if the user is on VPN or using a client other than AnyConnect.
Instead of verifying the device and identity by connecting to VPN, we can with ZTA instead verify and secure the device per session that is created.
All policies and administration of Secure Access are found in one combined portal, which makes it easier to manage – this also includes a strong API approach.
In the next few months, I will make another post focusing on Secure Access itself. In the meantime, do not hesitate to reach out to Conscia or me if you want to know more about the product.
Cisco Secure Firewall 4200 series
As the newest series in Secure Firewall, the 4200 series was also presented at Cisco Live 2023. It lies between the 4100 and 9300 series and is seen as a replacement for some of the outgoing models in these two series. In terms of its 1U form factor, it cannot replace the 9300 series if multiple security modules are necessary.
Fundamentally, the 3100 and 4200 series are very similar to each other, as they architecturally share the same platform – hence the reason why both platforms really set a new, high bar for performance, especially in light of being 1U.
Without going deep into the technical, the high crypto performance on these two series is primarily due to the introduction of a new inline crypto engine directly in the FPGA between the internal switch fabric and CPUs, thereby saving processor cycles and power.
The series’ smallest model performs no less than 65 Gbps*, which for most customers must be said to be a future-proof investment. There are also clustering options with up to 16 nodes – but let me be honest, it is hardly something we see used in most local European markets.
Secure Firewall 4200 series highlights:
- Offers 2 network modules for higher port capacity/speed
- Up to 200G interfaces (the platform also supports higher in the future)
- Hot-swap network modules and fail-to-wire (FTW) interfaces
- Redundant management ports – 2 x 1/10/25G interfaces (the only platform with 2xMGMT ports for redundancy)
- This also allows for splitting the event and control channel, thereby ensuring that events do not destroy the control channel, for example)
- Multi-instance with up to 34 instances (coming in a later release)
- Chassis Manager an integrated part of FMC as well as logical devices (as we see on the 3100 series)
Cisco FTD software – 7.2.4/5 and latest 7.4.0/7.4.1
Note that 7.4.x is the last version supported on the Firepower 2100 series
It is no secret that it has sometimes been a bit of a challenge with the Cisco FTD software in general. Back in the summer, Cisco’s management made a decision that something had to be done to remedy this. Therefore, it was announced that the focus would now be on stabilizing the platform, so hopefully, one would not have to worry about updates or sudden breakdowns. A massive investment has been made from Cisco’s side on this initiative, and personally, I also experience that there has been a huge progress in this area.
The initiative started with the release of 7.2.4, and will continuously be improved with 7.2.5 and 7.2.6. It is important to point out that this does not mean that 7.3.x or 7.4.x are forgotten – these releases also continuously receive the corrections from 7.2.x in their respective newer releases.
More than 100 firewall upgrades
At Conscia, we have, since the release of 7.2.4, focused a lot on upgrading customers from older versions up to 7.2.4/7.2.5. So far, we have collectively performed more than 100 firewall upgrades from versions before 7. This has resulted in a clear improvement for the customers, which confirms the measures that Cisco has taken.
The latest FTD software 7.4.0/7.4.1
Back in the middle of December (the 13th to be precise) we also got an early Christmas present from Cisco – namely version 7.4.1. And why is it more exciting than version 7.4.0 was? The answer is simple: 7.4.0 was only targeted at the 4200 series, and thus the remaining series had to wait for the release of 7.4.1.
Even though this recommended version is still 7.2.5, one should not necessarily be afraid to upgrade to 7.4.1, if one would like to use some of the new features herein. Below, I have outlined the new features in 7.4, which I see as most exciting and relevant:
- Encrypted Visibility Engine supports a more fine-tuned control and the ability to detect and block malware without decryption
- Introduced WAN Summary dashboard to FMC to create a better overview
- Cisco Dynamic Attribute Connector (CSDAC) is now an integrated part of the FMC running on containers, meaning it no longer needs to run on its own VM
- Device Management services (Syslog, SNMP, NetFlow, etc.) support per VRF segment
- Policy-based routing has been improved with the possibility for user identification, SGTags, and path monitoring now support HTTP probes
- Clientless Browser-Based ZTAA – replacement for the old ASA WebVPN method, just upgraded to 2024 standards with SAML and SSO integration. The solution is the same as we now see in Cisco Secure Access (this is clearly the coolest new feature!)
- Azure AD (Entra) user identification is now possible along with ISE (missed feature in many installations)
- Multi-instance possible for Secure Firewall 3100 series, FMC has taken over all functionality herein, and thereby no configuration in the Chassis Manager.
… Last but not least, it is important to note that NetFlow has become an FMC function, and therefore you should make sure to remove any FlexConfig that includes NetFlow, before the first deployment!
About the author
Related












