Blog
Enumeration Attacks: A Deep Dive into Threat Actors Generating Valid Payment Data
Enumeration attacks, especially banking identification number (BIN) generation attacks, enable threat actors to produce and validate payment card numbers. These attacks, while not new, are high-effort and offer low rewards. However, they can still pose a threat to the payments ecosystem. Understanding Enumeration Attacks Enumeration attacks involve “guessing” the correct combinations of values, with the attacker knowing at least […]

Enumeration attacks, especially banking identification number (BIN) generation attacks, enable threat actors to produce and validate payment card numbers. These attacks, while not new, are high-effort and offer low rewards. However, they can still pose a threat to the payments ecosystem.
Understanding Enumeration Attacks
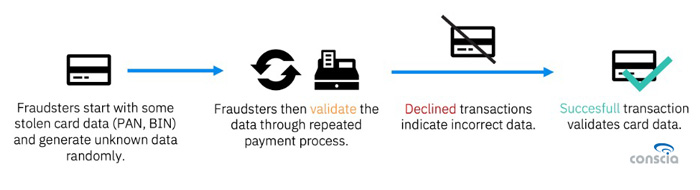
Enumeration attacks involve “guessing” the correct combinations of values, with the attacker knowing at least one correct value. For example, using BIN generation, a subset of enumeration attacks, attackers can use algorithms like the Luhn Algorithm to generate a valid payment card number.
Research from Newcastle University has highlighted that cybercriminals can use enumeration attacks to identify unknown payment card data elements. They can start with one piece of data, such as the payment card’s primary account number (PAN), and make multiple attempts on e-commerce sites with minimal verification requirements to guess other values. This method can potentially reveal a card’s expiration date, CVV2, and address details within seconds.
How it Works
Threat actors, in practice, often obtain complete card data sets, including personal identification information (PII), when they buy payment card data from dark web shops. However, BIN generation attacks offer them an alternative method to get valid card data without making such purchases.
The process generally involves:
- Generation: Use the card issuer’s BINs to produce potential card numbers.
- Validation: Confirm if the generated numbers are valid.
- Monetization: Use the valid card data for fraudulent activities.
Validating Generated Payment Card Data
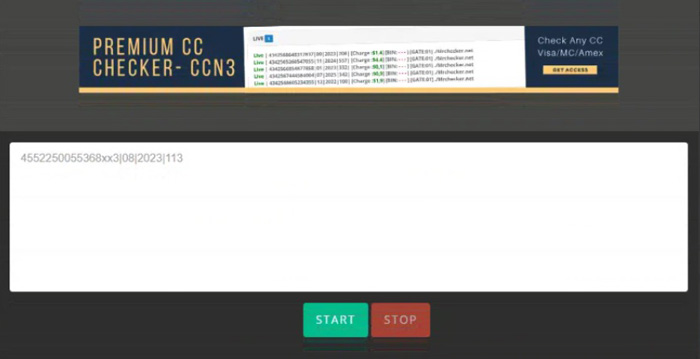
For attackers, validating the generated card numbers is crucial. They can easily produce tens of thousands of valid card numbers from a single BIN. However, these numbers must be correctly associated with other card data values, such as expiration dates and CVV2, to be used fraudulently.
Methods used for validation include:
- Using Stripe’s Live Mode Secret API Key: Attackers can exploit the Stripe secret API key to validate the card data obtained from enumeration attacks.
- Utilizing Free Online Checker Services: A growing number of free card-checking services are emerging, making card-testing services more accessible.
- Employing Ready-to-Go Checker Software: Some threat actors sell software that others can use to validate generated card data.
Mitigating the Risks
To address the threats posed by enumeration attacks:
- Card issuers should institute velocity checks to detect unusual transaction spikes within certain BIN sets.
- Merchant acquirers should encourage or require merchants to adopt more stringent verification processes.
- All parties involved should adopt and disseminate best practices, like Visa’s 2021 guidelines against enumeration attacks, and use automated anti-fraud systems.
Conclusion
While threat actors can obtain valid payment card data through the methods described, the success of these fraudulent schemes largely depends on the ability to exploit weaknesses in merchant verification processes. As merchants adopt more rigorous verification methods, the effectiveness of enumeration attacks will likely diminish. Nevertheless, the ongoing evolution of cyber threats means stakeholders must remain vigilant and continually adapt their defenses.

What’s New in Cisco Network Security: Strategy & Latest Solut(…)
Delve into Cisco’s network security roadmap and learn about new developments in traffic encryption, dynamic security rules, and the innovative 3k FTD Secure series in our upcoming webinar! Cisco Netwo…
About the author

David Kasabji
Principal Threat Intelligence Analyst
David Kasabji is a Principal Threat Intelligence Analyst at the Conscia Group. His main responsibility is to deliver actionable intelligence in different formats according to target audiences, ranging from Conscia’s own cyberdefense, all the way to the public media platforms. His work includes collecting, analyzing, and disseminating intelligence, reverse engineering obtained malware samples, crafting TTPs […]
Related











