Blog
Lateral Movement – advanced cyber crime
Lateral Movement is a technology that cybercriminals use to move in a hijacked network. The movements look like normal network traffic, which allows them to move freely in the search for the information they are looking for. In Lateral Movement, the attacker uses various tools and techniques to gain higher privileges and access. As they […]

Lateral Movement is a technology that cybercriminals use to move in a hijacked network. The movements look like normal network traffic, which allows them to move freely in the search for the information they are looking for.
In Lateral Movement, the attacker uses various tools and techniques to gain higher privileges and access. As they get to know the network, they can finally access more accurate documentation of applications, dependencies, and the network than the IT department itself.
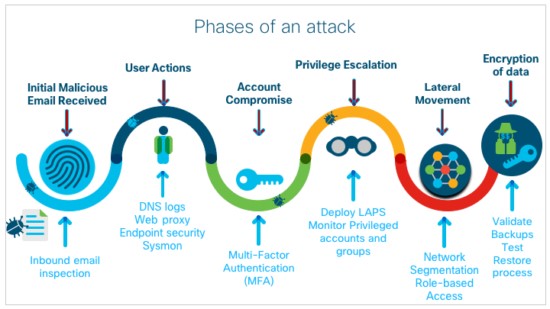
If the administrative rights are cut so that the attacker gets full access to the system, it is almost impossible to detect that the system is under the control of an outsider. And if the attack is detected, it is often already ended, and the attackers have already left the system with the information they were looking for.
Every day new systems are attacked and hijacked. The attackers can be sophisticated and targeted or use automated programs that exploit known bugs and weaknesses in machines, software, and end-users.
It is more important than ever to have a security team that can detect the lateral movement quickly and safely. Lateral Movement is part of the steps in the attack chain most hackers need to go through – see the movie about Kill Chain we made with Cisco here (in Swedish).
How can you detect and limit the damage caused by lateral movement?
Traditional security tools generate large amounts of logs which means you can easily miss important information. If you do not detect attack patterns, you also miss the opportunity to stop the spread of malicious software.
By supplementing the traditional shell protection with tools that correlate and analyze application behavior both in the network and at the endpoints, you get the opportunity to detect abnormal traffic. Machine learning / AI can also be introduced to a greater or lesser extent to automate responses to detected threats.
By creating a profile for the normal state of the network, it becomes easier to detect deviations and to continuously address them. For instance, if an endpoint is identified as infected, it can be quarantined automatically while creating rules in the network to stop similar attacks. The quarantine zone has limited access and allows an administrator to fix the endpoint and move it back to full operation.
About the author
Related











