Blog
Microsoft to Require MFA for Azure Portal, Entra Admin Center, and Intune Admin Center – Are You Ready?
Starting October 15, 2024, Microsoft will require Multi-Factor Authentication (MFA) for all sign-ins to Azure Portal, Microsoft Entra Admin Center, and Intune Admin Center. This blog explains what you need to do to meet the new MFA requirements. MFA (Multi-Factor Authentication) is one of the key security mechanisms for protecting your cloud identities from cyberattacks […]
Starting October 15, 2024, Microsoft will require Multi-Factor Authentication (MFA) for all sign-ins to Azure Portal, Microsoft Entra Admin Center, and Intune Admin Center. This blog explains what you need to do to meet the new MFA requirements.
MFA (Multi-Factor Authentication) is one of the key security mechanisms for protecting your cloud identities from cyberattacks and the de-facto user authentication standard. It is a best practice, and we strongly recommend implementing it to verify user identity and credentials.
If your organization is using Microsoft Azure, Microsoft Entra, or Microsoft Intune, you will soon have to require MFA to manage these services. Are you or your IT Admins prepared?
Before you give yourself a confident nod, let’s check a few things:
- Are you enforcing Multi-Factor Authentication (MFA) for all your Microsoft Entra accounts that access company resources?
- No? Well, surely you’re using MFA for the Azure Portal or Microsoft Entra Admin Center, right?
- Still no?
Starting October 15, 2024, MFA will no longer be optional. Microsoft will require it for any sign-ins to:
- Azure Portal – https://portal.azure.com/
- Microsoft Entra Admin Center – https://entra.microsoft.com/
- Microsoft Intune Admin Center – https://intune.microsoft.com/
- Azure Command-line Interface (Azure CLI)
- Azure PowerShell
- Azure Mobile App
- Infrastructure as Code (IaC) tools
There will be no exceptions to this rule – not even for your emergency access (break-glass) accounts (and you have at least two break-glass accounts set up in your Microsoft Entra tenant, right?).
If this is news to you, or you’ve only heard rumors about the upcoming MFA enforcement, or you haven’t set up break-glass accounts – now’s the time to take action. Keep reading to make sure you’re ready
Background
For customers using Microsoft Entra who didn’t have Conditional Access enabled, MFA was automatically enforced in May 2022 with the rollout of Security Defaults. This mainly affected smaller businesses without Microsoft Entra P1 or P2 licenses, where security teams might be limited, making them easier targets for attackers. Consequently, identity-related attacks dropped by 80% after the Security Defaults rollout.
For larger organisations that need more flexible and detailed security controls, Conditional Access is typically the best approach for protecting cloud identities. With conditional access policies (CAPs), you can define rules that determine who gets access to what and under which conditions. When properly implemented, CAPs offer strong protection against cyberattacks.
So far, the best practice/recommendation was to exclude break-glass accounts from CAPs that require MFA at sign-in, even though these accounts often hold powerful permissions, like a permanently assigned Global Administrator role. However, with Microsoft’s new MFA requirement across all tenants, these emergency accounts – typically exempt of MFA – will now be affected as well.
Break-glass accounts should only be used in emergencies and as a last resort, for example, when you can’t log in with your regular admin account due to a service outage or a breach. As an additional security mechanism next to MFA, we recommend you set up detection rules to trigger alerts when an emergency or break-glass account is used. If you haven’t done this yet, please contact our security team, and we can advise you on how to deploy it.
How to enable MFA in Microsoft Entra Admin Center?
Before October 15, 2024, when Microsoft will start requiring MFA to access Azure Portal, Microsoft Entra Admin Center, and Microsoft Intune Admin Center, you should do the following configuration in your Microsoft Entra Admin Center portal.
First, check if you’ve turned on Security Defaults or if you’re using Conditional Access. Just follow these simple steps:
1. Open your web browser and navigate to https://entra.microsoft.com. Log in using an account that has at least the Security Administrator role assigned.
2. On the left side of the screen, click Identity, then go to Overview, and finally, click on Properties.
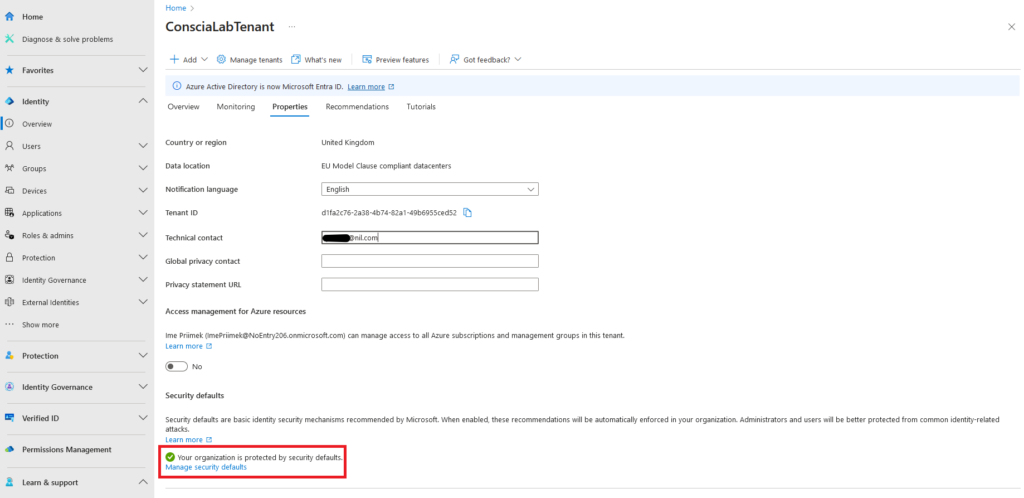
As shown in the screenshot above, if Security Defaults are enabled, you’ll find the information at the bottom of the Properties page.
Microsoft Entra tenants with Conditional Access policies configured will see something like the screenshot below.
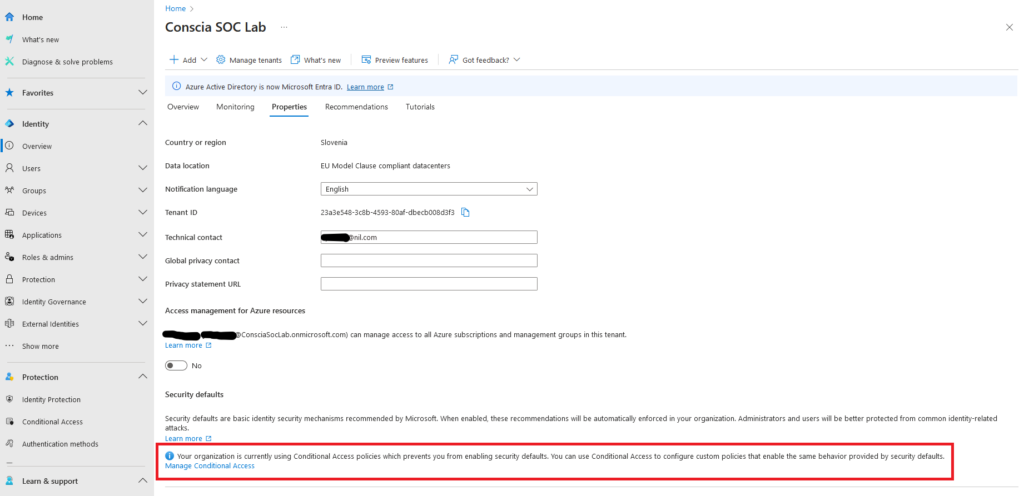
If your tenant uses Conditional Access Policies, you must identify accounts that have access or have signed in to Microsoft Entra Admin Center, Azure Portal, or Intune Admin Center.
Identify Accounts
In this chapter, we’ll show you how to identify user accounts that have signed in to the Microsoft Entra Admin Center, Azure Portal, or Microsoft Intune Admin Center using Insights and a reporting workbook.
1. Open your web browser and navigate to https://entra.microsoft.com. Log in with an account that has at least the Security Administrator role assigned.
2. On the left side, click Identity, then go to Protection, select Conditional Access, and finally click on Insights and Reporting.
Important: To see results in Insights and Reporting, you must configure the forwarding of Entra ID Sign-In Logs to a Log Analytics workspace.
3. In the User Sign-ins tab, set the attributes as shown in the screenshot below.
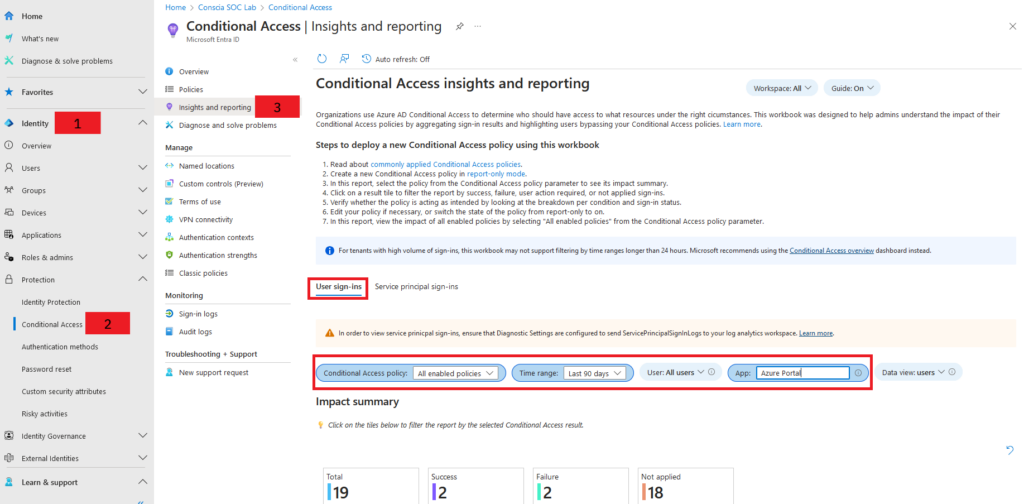
- Set “Conditional Access policy” to “All enabled policies”
- Set “Time range” to “Last 90 days” (longest time range available)
- Set “User “to “All users”
- Set “App” to “Azure Portal”
Results will appear under the Impact Summary. Be sure to review the Failure and Not Applied results in detail.
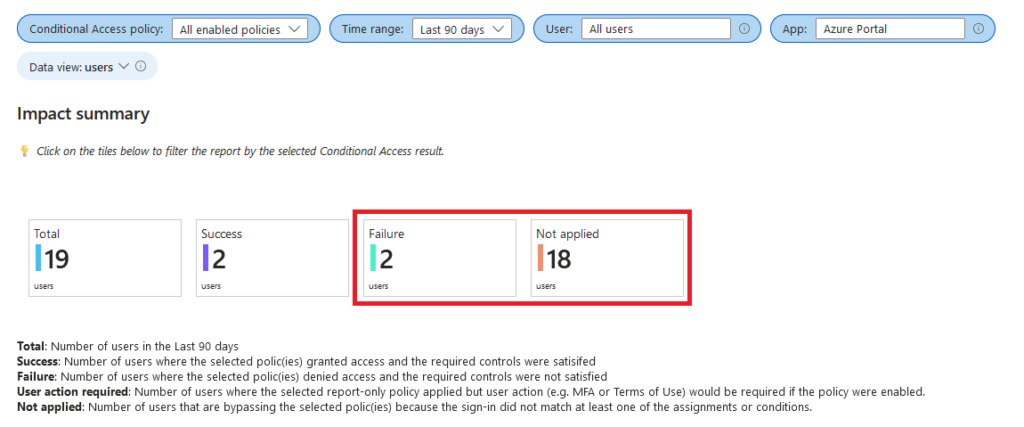
For tenants using Security Defaults, user accounts should already be required to authenticate using strong authentication.
If you click on Not Applied and scroll further down, you should see UserPrincipalNames.
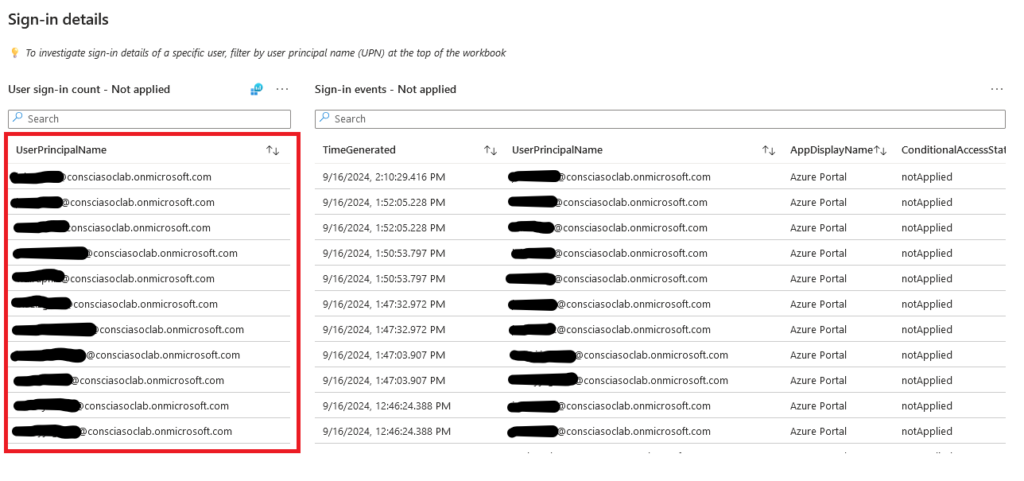
These are the user accounts that signed in to Microsoft Entra admin center, Azure Portal, or Microsoft Intune Admin Center in the last 90 days.
For accounts that haven’t accessed any of the mentioned admin portals in the selected time frame – most likely, these are your break-glass accounts defined for the Entra tenant, review the Conditional Access Policy enforcing MFA and check if any user accounts have been excluded.
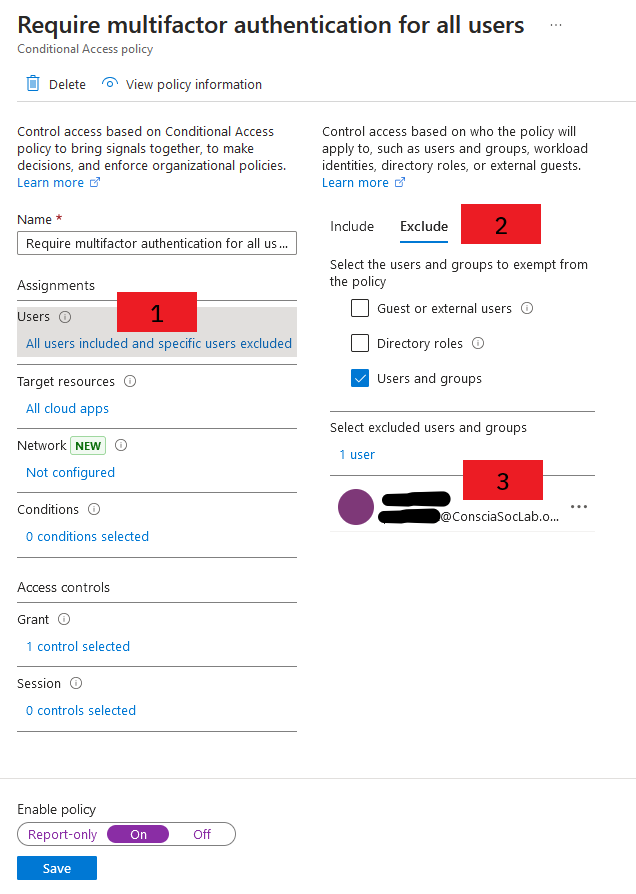
Select Authentication Method
Once you’ve gathered all the accounts and confirmed they have a legitimate reason to access the admin portals, you’ll need to decide which type of strong authentication to permit.
There are two main types of strong authentication methods:
- Strong Authentication with Two Factors, also known as MFA (Multi-Factor Authentication): This typically requires a username and password as the first factor, followed by a second factor, such as SMS, voice, Microsoft Authenticator number matching, or software/hardware OTP.
- Password-less Strong Authentication, also known as Phishing-resistant Authentication: This includes methods like Windows Hello for Business, FIDO2 security keys, Passkeys with Microsoft Authenticator, and Certificate-Based Authentication (CBA).
Up until now, we’ve focused on MFA enforcement. It’s important to clarify that Password-less Strong Authentication will also fully meet the requirements.
We strongly recommend going a step further by implementing phishing-resistant authentication methods, as they offer enhanced protection against token replay attacks, including Adversary-in-the-Middle (AiTM) attacks.
When evaluating which authentication type to use in your Microsoft Entra tenant, it’s important to consider the additional services required for successful authentication.
For example, after a user passes the first authentication factor – username and password (provided by the native Entra Authentication Service) – the Conditional Access Policy may require the user to complete an MFA challenge (in this case, Azure MFA Service is activated). The user then receives a one-time password (OTP) via SMS to their mobile phone (delivered by the phone carrier), and finally, enters the OTP in the authentication form.
Each additional service involved can reduce the resiliency of the authentication process. Therefore, it’s best to minimize the number of dependencies, especially when selecting an authentication method for emergency or break-glass accounts. For these critical accounts, it’s essential to avoid relying on extra services, ensuring the authentication process remains as resilient to outages as possible.
The figure below outlines the dependencies for each authentication method available in Microsoft Entra.
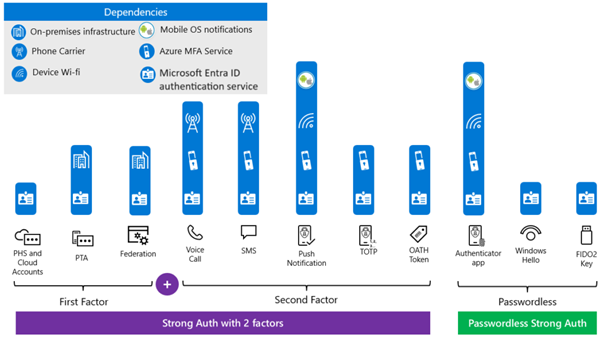
Additionally, when choosing an authentication method for your break-glass/emergency accounts, keep in mind that these accounts shouldn’t be tied to a specific person or device. The most reliable authentication method for break-glass accounts is a FIDO2 security key.
TL;DR: Enable MFA in 5 Steps
In summary, below are the 5 main action points you should complete before October 15 to meet the new Microsoft MFA requirements:
- Verify whether Security Defaults are enabled or if Conditional Access is being used in your Microsoft Entra tenant.
- Identify all user accounts that are interactively accessing the Microsoft Entra Admin Center, Azure Portal, or Microsoft Intune Admin Center.
- Choose an appropriate authentication method for the identified user accounts.
- Implement a Conditional Access Policy that enforces the selected authentication method for those accounts.
- Register the FIDO2 security key(s) as the authentication method for your break-glass/emergency accounts.
By following these 5 steps, you’ll be ready for the upcoming MFA enforcement.
Should you need any help preparing your Microsoft Entra tenant, do not hesitate to contact our team, and we’ll be happy to assist you.
Also, if you are for some reason unable to setup MFA by October 15, you can request an extension for your Entra tenant until March 15, 2025.
About the author

Jan Češčut
Cybersecurity Analyst
Jan Češčut, MCSE, GCFA, CQURE Certified Windows Security Master, is an analyst and a cybersecurity advisor at NIL´s Security Operations Center (SOC). He mostly focuses on endpoints and Microsoft security technologies, and is also one of the leading domestic experts for Azure Sentinel, Microsoft Defender for Identity, Microsoft Defender for Endpoint, and Microsoft Cloud App […]
Related











