Blog
Ransomware-as-a-Service: An infamously lucrative business model
Ransomware as a type of malware is not a 21st century invention. We can trace it back to 1989 when Joseph Popp wrote the first known ransomware known as PC Cyborg Trojan. However, since 2010 ransomware attacks really started to pick up in intensity, and that makes sense when you consider that in 2021 only, cybercriminals […]

Ransomware as a type of malware is not a 21st century invention. We can trace it back to 1989 when Joseph Popp wrote the first known ransomware known as PC Cyborg Trojan. However, since 2010 ransomware attacks really started to pick up in intensity, and that makes sense when you consider that in 2021 only, cybercriminals earned over $20 billion.
With such tempting numbers, new business models started to appear, one of which is known as RaaS (Ransomware-as-a-Service). RaaS is a business model where affiliates pay to launch ransomware attacks developed by RaaS operators.
RaaS Kit Pricing
These RaaS Kits are being offered on Dark Web, in the same way, you would do online shopping. The RaaS operators have dedicated websites with customer support, supporting forums, reviews, etc. The RaaS Kit prices range from around 50 EUR to thousands of euros. If we recall that the average ransom demand in 2021 was $6 million, these are very affordable numbers. The payment methods vary, but the common ones include:
- Subscription model (Monthly, yearly)
- Profit sharing
- One-time license fee
Sophisticated RaaS operators offer modern website portals that are easy to use to setup affiliates as quickly as possible.
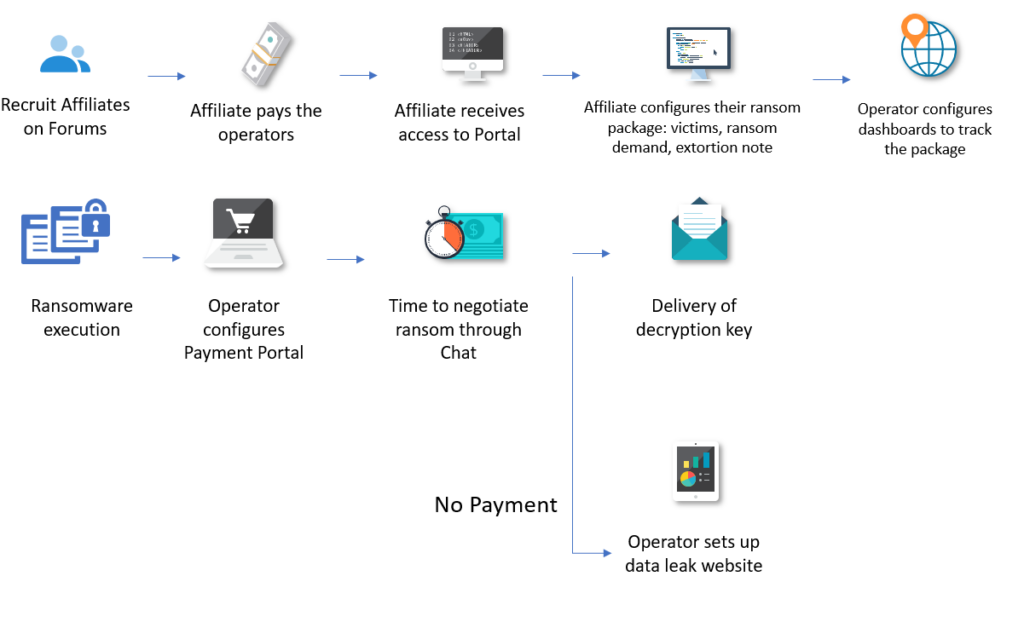
Typical flow of RaaS Attack
Hive Ransomware is becoming increasingly popular among affiliates due to its ease of use and modern web applications. Affiliates can generate a unique version of ransomware in less than 15 minutes. The single largest ransom demand belongs to Hive, where they asked for $240 million in November 2021 from MediaMarkt.
This is an example of Hive’s Affiliates Website Portal:
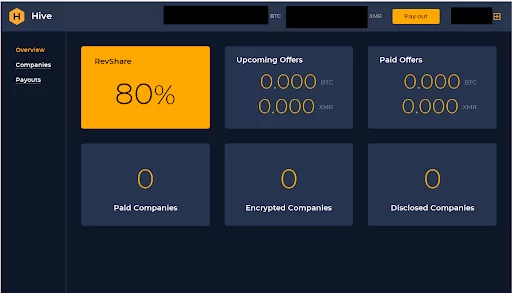
Source: The Hive Affiliate Program home page
They also provide affiliates with a nice Customer Support portal that victims are able to login into to perform their negotiations for the decryption key.
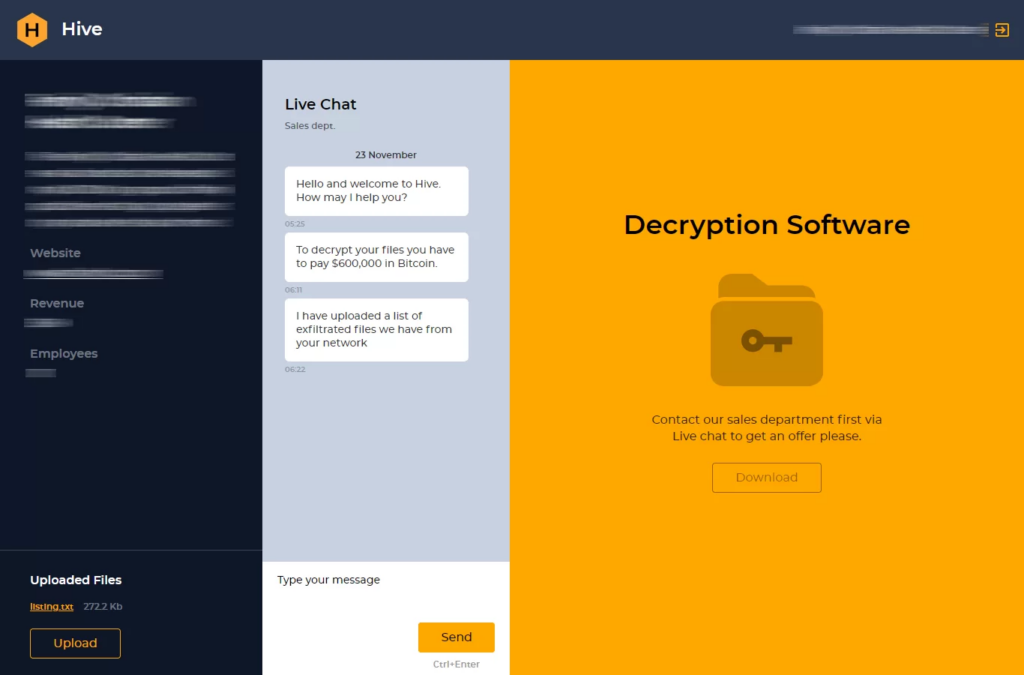
Source: Group IB – Inside the Hive
You can see that the portal is split into 3 columns, where:
- First column lists all the information about the victim company / organization, including their revenue and number of employees
- Second column is used for Live Chat interaction with Operator and/or affiliate
- Third column is reserved for downloading decryption software after successful payment
Finally, if ransom demands are not met or fulfilled – the operator will leak the stolen data on one of their dedicated leak websites.
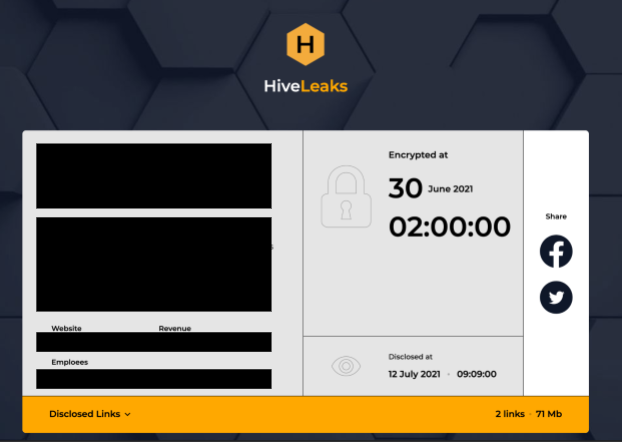
Source: HiveLeaks website
Of course, all these websites are hosted on dark web.
Examples of RaaS
- DarkSide
- REvil
- Hive
- LockBit
How to prevent RaaS Attacks
Preventing RaaS attacks is the same as preventing ransomware attacks as the difference lies only in the business model.
Apply these practices to the greatest extent possible based on the availability of organization resources:
- The most important best practice you can do is to maintain encrypted offline backups. Sophisticated ransomware will try to find and delete any accessible backups otherwise.
- Create, maintain, and exercise a basic cyber incident response plan
- Conduct regular vulnerability scanning
- Regularly patch and update software to the latest version
- Employ best practices for use of remote desktop services and audit the network for any suspicious usage
- Disable or block SMB protocol outbound and remove or disable outdated versions of SMB
- Maintain up to date anti-malware software and signatures
- Use application whitelisting to ensure only authorized software can run on your systems
- Consider deploying IDS and EDR systems to quickly detect potential intrusions
- Understand that adversaries may exploit third parties to gain access to your environment, so make sure to apply cyber hygiene of third parties and managed service providers
- Employ MFA for all services to the extent possible
- Apply the Least privilege principle
- Make sure your network is segmented appropriately to limit the capabilities of lateral movement
- Restrict usage of scripting tools if possible (PowerShell, Python, …)
- If possible, performing long-term monitoring of your network activity and create a baseline of it so you can compare it during later stages to detect any anomalous behavior
If you need help with any of these, Conscia can help you with hardening your environments, and with our Conscia Cyberdefense service, we can monitor your environments for potential intrusions now and in the future.
Please reach out to your nearest Conscia market for any questions
About the author

David Kasabji
Principal Threat Intelligence Analyst
David Kasabji is a Principal Threat Intelligence Analyst at the Conscia Group. His main responsibility is to deliver actionable intelligence in different formats according to target audiences, ranging from Conscia’s own cyberdefense, all the way to the public media platforms. His work includes collecting, analyzing, and disseminating intelligence, reverse engineering obtained malware samples, crafting TTPs […]
Related











