Blog
Cloud Storage Risk Assessment: Our privacy rests… at risk?
Cloud storage and hosting have become a common way of storing your and your organization’s sensitive data in today’s world. Cloud storage refers to a data storage service provided by cloud computing providers, where digital data is stored and managed on remote servers accessed via the Internet. Instead of storing data on a local hard […]

Cloud storage and hosting have become a common way of storing your and your organization’s sensitive data in today’s world.
Cloud storage refers to a data storage service provided by cloud computing providers, where digital data is stored and managed on remote servers accessed via the Internet. Instead of storing data on a local hard drive or physical storage device, cloud storage enables users to store and retrieve data from these remote servers, typically maintained and managed by third-party service providers.
Key characteristics of cloud storage include:
- Remote Accessibility: Users can access their stored data from anywhere with an internet connection, using various devices such as computers, smartphones, and tablets.
- Scalability: Cloud storage solutions can be easily scaled up or down to accommodate changing storage needs, eliminating the need for significant hardware investments.
- Redundancy and Reliability: Reputable cloud storage providers often employ redundant data storage and backup systems to ensure data availability and durability.
- Data Security: Cloud storage services typically include security features such as encryption, access controls, and authentication to protect stored data from unauthorized access.
- Backup and Recovery: Many cloud storage services offer automated backup and data recovery features, allowing users to recover lost or corrupted files.
- Collaboration Tools: Cloud storage often includes features like file sharing, version control, and real-time editing, facilitating teamwork and productivity.
- Cost-Efficiency: Users only pay for the storage capacity they use, avoiding upfront hardware costs and infrastructure maintenance.
Popular examples of cloud storage providers include Google Drive, Dropbox, Microsoft OneDrive, Amazon S3, and iCloud, each offering various storage plans and features to cater to individual users, businesses, and organizations.
Cloud Storage Cyber Attacks
Before diving into the risk assessment of Cloud Storage services, let’s examine recent cyber-attack trends towards Cloud Storage services.
Our sources have tracked nearly 7000 cyber-attacks on Cloud Storage services this year (2023) so far. As shown in the graph below, we notice that as Cloud Storage gets increasingly popular (if not already something common), cyber-attacks are consistent throughout the year.
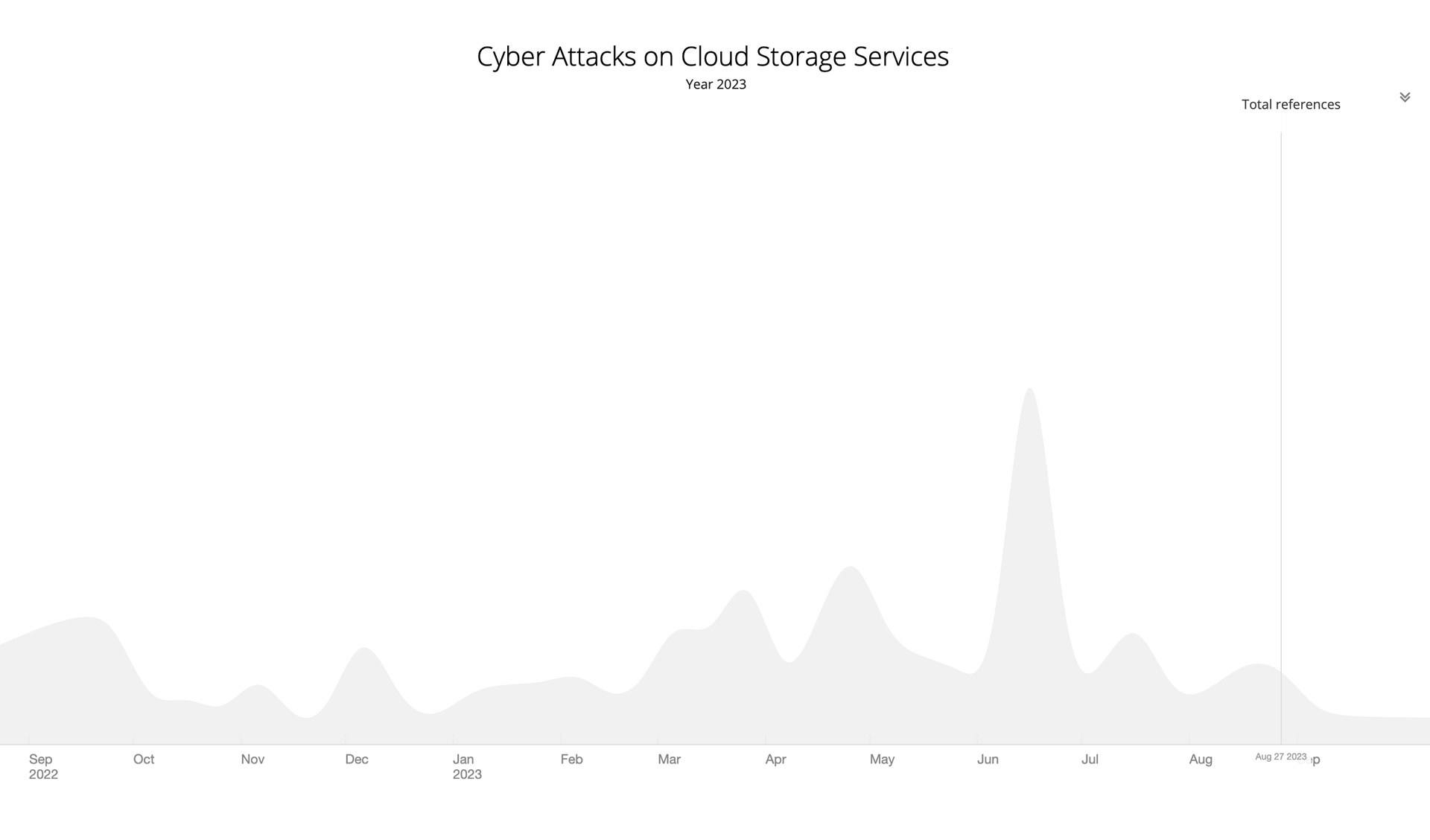
Cloud Storage services are targeted by several different cyber-attacks, ranging from exploiting discovered vulnerabilities against the products, phishing, DDoS, brute force attacks, and many more. It is hard to pinpoint the prevalent technique, but on the other hand, that makes sense – cloud storage hosts today’s sensitive data for almost any organization out there, thus making it lucrative for threat actors to gain access.
We did notice that phishing tends to stand out the most, but phishing is also the number one attack vector in general cyber-attacks (not just against cloud storage services specifically). Perhaps we could divulge a correlation here: It could be plausible that phishing is the number one attack vector because it is mainly used to gain access to sensitive data, which in today’s world, most of the time, is hosted in some sort of cloud storage. Further research would be required to accept this hypothesis, but it is good food for thought.
A brief Cloud Storage Risk Assessment
As convenient as it may sound to host your data at a certain provider and transfer the risks to them – we are still talking about the sensitive data we want to keep secure and private. Thus, it is important to understand the risks associated with cloud storage services.
Below, we conducted a brief risk assessment for cloud storage services.
1 Data Breach Risk:
- Threat: Unauthorized access or data breaches by cybercriminals.
- Risk: High. Cloud storage services are attractive targets for hackers due to the volume of data they host.
- Mitigation: Implement strong access controls, encryption, and regular security assessments.
2 Data Loss Risk:
- Threat: Accidental deletion, service provider errors, or system failures.
- Risk: Moderate. Service providers usually have robust data backup and recovery mechanisms.
- Mitigation: Regularly backup data, use redundant storage, and ensure the CSP has backup and recovery options.
3 Compliance Risk:
- Threat: Failure to comply with data protection regulations (e.g., GDPR, HIPAA) due to improper handling of sensitive data in the cloud.
- Risk: High. Non-compliance can result in hefty fines and legal consequences.
- Mitigation: Choose a CSP with relevant compliance certifications and implement appropriate data protection measures.
4 Vendor Lock-In:
- Threat: Dependence on a single CSP, making it challenging to migrate data to another provider or back to on-premises storage.
- Risk: Moderate. Transition costs and complexities may arise if you decide to change providers.
- Mitigation: Evaluate the CSP’s data export policies and consider using cloud-agnostic storage formats and technologies.
5 Insider Threats:
- Threat: Malicious activities or negligence by employees or service provider staff.
- Risk: Moderate. Insider threats can compromise data security if not adequately managed.
- Mitigation: Implement strict access controls, conduct employee training, and monitor user activities.
6 Legal and Jurisdiction Risks:
- Threat: Legal disputes or data access requests from foreign governments based on where the CSP stores data.
- Risk: Moderate to High. It depends on the CSP’s data center locations and the data’s sensitivity.
- Mitigation: Choose CSPs with transparent data storage practices and understand data jurisdiction implications.
7 Availability Risk:
- Threat: Downtime or service interruptions affecting access to data.
- Risk: Moderate. Most reputable CSPs offer high availability, but incidents can still occur.
- Mitigation: Use CSPs with strong service-level agreements (SLAs) and consider multi-cloud or hybrid cloud setups for redundancy.
8 Cost Management:
- Threat: Unexpected cloud costs due to data storage, bandwidth, and additional services.
- Risk: Moderate. Costs can escalate if not properly monitored and managed.
- Mitigation: Implement cost management tools, monitor resource usage, and regularly review your cloud spending.
9 Security Misconfigurations:
- Threat: Inadequate configuration of cloud storage services leading to data exposure.
- Risk: Moderate. Misconfigurations are common and can result from human error.
- Mitigation: Regularly audit and review configurations and use automation to enforce security policies.
10 Third-Party Integrations:
- Threat: Security vulnerabilities introduced by third-party applications or services integrated with cloud storage.
- Risk: Integrations can pose risks if not properly vetted.
- Mitigation: Assess the security of third-party integrations and ensure they adhere to best practices.
11 Evolving Threat Landscape:
- Threat: Constantly evolving cyber threats that may outpace security measures.
- Risk: The threat landscape is dynamic and requires ongoing vigilance.
- Mitigation: Stay updated on emerging threats, regularly update security measures, and invest in threat intelligence.
In conclusion, while cloud storage offers numerous benefits, it has inherent risks. Effective risk mitigation involves a combination of careful CSP selection, robust security practices, ongoing monitoring, and compliance with data protection regulations. Organizations must assess these risks carefully and implement appropriate safeguards to protect their sensitive data in the cloud.
Cloud Storage Threat Classification Frameworks
Frameworks are great guidelines for constructing policies and procedures within our organization to address certain risks. When discussing cybersecurity threat detection and classification, we will surely stumble upon the MITRE ATT&CK Framework, which serves the cybersecurity community with great unified classification options through their Tactics & Techniques matrix.
Perhaps not many of you have heard of Microsoft’s Cloud Storage Matrix, though. For those of you who have not, here is a short introduction. In April 2021, Microsoft released version one of Cloud Storage Matrix to reflect techniques used specifically against cloud storage systems but still mapped to well-known MITRE ATT&CK Tactics.
The methodology used by Microsoft
Microsoft researchers found that MITRE ATT&CK lays a great foundation for tracking techniques across the tactics for the cyber threat landscape. Still, they found some differences when researching techniques used in cloud storage attacks, which are now reflected in their Cloud Storage Matrix. Aiming to address the entire attack surface for storage, from data loss prevention (DLP) and sensitive content exposure to uncovering malicious content distribution over a file share Server Message Block (SMB), Microsoft adjusted the enterprise tactics to fit a data service.
The initial version can be reviewed in their article.
Cloud Storage Matrix new techniques added
As said earlier in the article, Cloud Storage Matrix replicates the MITRE ATT&CK’s tactics but assigns some new techniques specific to cloud storage attacks.
In the picture below, we share Microsoft’s capture of newly added techniques to version two of its release.
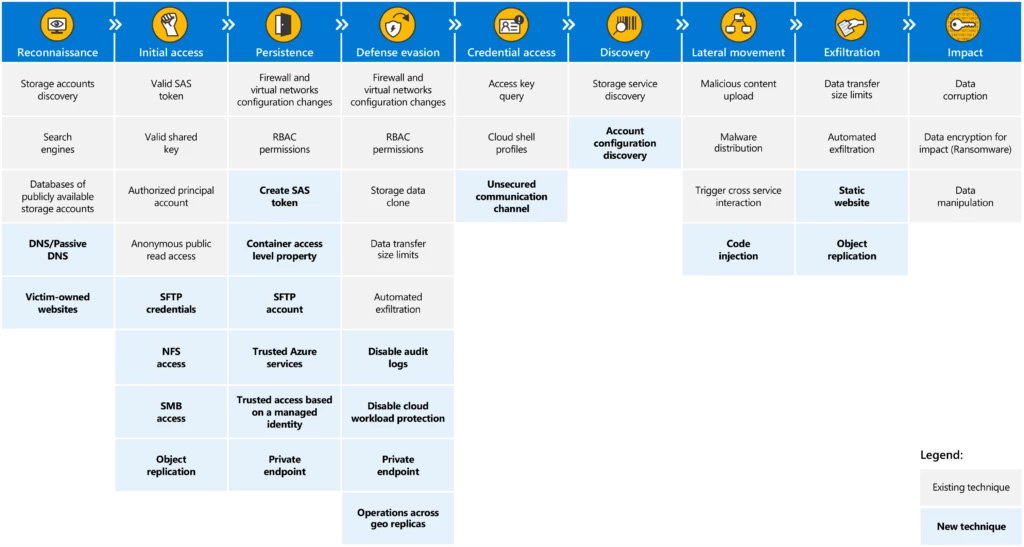
Microsoft points out the following techniques as noteworthy in this release:
- Object replication – This allows attackers to maliciously misuse the object replication feature in both directions by either using outbound replication to exfiltrate data from a target storage account or inbound replication to deliver malware to the target account.
- Operations across geo replicas – Helps attackers evade defenses by distributing operations across geographical copies of storage accounts. Security solutions may only have visibility into parts of the attack and may not detect enough activity in a single region to trigger an alert.
- Static website – Allows attackers to exfiltrate data using the “static website” feature, a feature provided by major storage cloud providers that less experienced users can often overlook.
For more detailed information and to examine other new techniques added to the matrix, we invite you to read Microsoft’s official security blog on Cloud Storage Matrix.
What are the benefits of such Matrices?
Now that we have shown you the existence of another matrix, other than MITRE’s, that you may have been aware of, it is good to remember why these matrices are helpful.
These matrices offer a comprehensive repository of adversary behaviors and intelligence, providing a standardized language for cybersecurity professionals. This common framework facilitates a deep understanding of adversary actions, enabling proactive defense measures and attack prevention.
One of their key advantages lies in aiding risk assessment. Red teamers and cyber defenders can leverage them to categorize attacks, evaluate their organization’s risk posture, and reinforce security measures effectively.
Furthermore, they enhance post-compromise detection. By outlining potential attacker maneuvers, security teams can promptly respond with targeted actions, minimizing the impact of breaches.
Such frameworks also play a crucial role in supporting Threat Hunting initiatives. Threat hunters gain insights into diverse adversary techniques, empowering them to proactively seek out threats and gauge their environment’s readiness against specific attack strategies.
Lastly, they foster collaboration among analysts and defenders. By comparing adversary tactics and threat group behaviors, teams can work together to identify optimal detection and mitigation strategies, ultimately bolstering threat mitigation efforts.
Conclusion
In today’s data-driven world, adopting cloud storage services has become ubiquitous. However, with the conveniences of cloud storage come potential risks that should not be overlooked. As we’ve explored in this article, these risks include data breaches, privacy concerns, compliance challenges, and service disruptions.
While these risks are natural, it’s important to emphasize that they can be effectively mitigated with a proactive and well-thought-out approach to security and data management. Implementing strong encryption, access controls, and multi-factor authentication can significantly enhance the security of your stored data. Regularly monitoring for suspicious activities and staying informed about compliance requirements are essential steps in safeguarding sensitive information.
Furthermore, choosing a reputable cloud storage provider with a proven track record in security and compliance can go a long way in minimizing these risks. Assessing the provider’s security features, data protection measures and disaster recovery capabilities should be part of your selection process.
Ultimately, the benefits of cloud storage, including cost-efficiency, scalability, and remote accessibility, can be harnessed while managing the associated risks effectively. By adopting a security-first mindset, staying informed about evolving threats, and implementing best practices, individuals and organizations can confidently embrace the advantages of cloud storage while keeping their data safe and secure.

Danish cloud-hosting provider hit by devastating ransomware attack.
Danish cloud-hosting company were hit by ransomware attacks, resulting in significant customer data loss and system shutdowns.
About the author

David Kasabji
Principal Threat Intelligence Analyst
David Kasabji is a Principal Threat Intelligence Analyst at the Conscia Group. His main responsibility is to deliver actionable intelligence in different formats according to target audiences, ranging from Conscia’s own cyberdefense, all the way to the public media platforms. His work includes collecting, analyzing, and disseminating intelligence, reverse engineering obtained malware samples, crafting TTPs […]
Related











