Blog
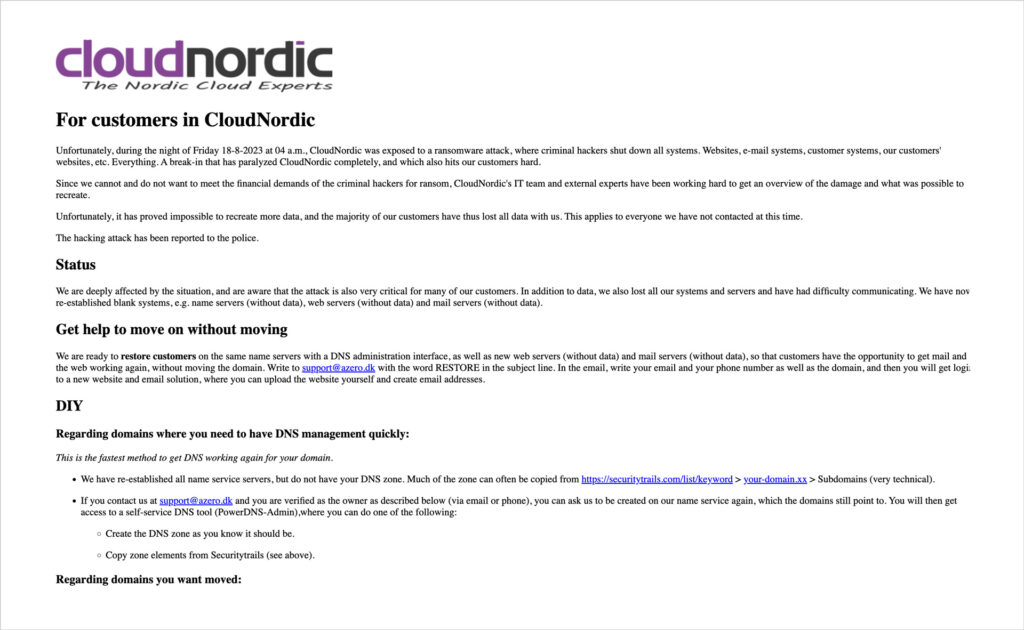
Danish cloud-hosting provider hit by devastating ransomware attack.
Danish cloud-hosting company were hit by ransomware attacks, resulting in significant customer data loss and system shutdowns.

Danish cloud-hosting companies CloudNordic and AzeroCloud were hit by ransomware attacks, resulting in significant customer data loss and system shutdowns, according to their notification on the (now changed) Danish landing page of CloudNordic’s website.
The attack affected websites, email services, and customer sites. Both brands, owned by the same company, Certiqa Holding (which also owns Netquest), experienced the attacks on August 18, 2023. In a statement to customers, CloudNoridc highlighted that they would not pay the ransomware demands and that the “majority of customers have lost all data.” At the time of writing, no ransomware group has claimed responsibility or acknowledged their involvement in the cyberattack.
What Happened?
The initial cause of the ransomware attack remains unclear. Based on what CloudNordic shared on their website (in Danish), we can assume that they have had an infected server segment for a while but did not notice it. We believe this could be due to a lack of security visibility into that server’s segment.
During their server migration, the infected servers were also migrated. However, according to CloudNordic, the infected servers were unintentionally connected to the internal network managing all servers, thus allowing the threat actors to penetrate central administration and backup systems through the internal network.
What we know about the defensive capabilities
With the given information, it is fair to assume that the organization might not have had great visibility into its servers or endpoints. Albeit mentioning the prevention security products, such as firewalls and antivirus, there was probably a lack of monitoring capabilities for potential intrusion events. This does not mean that the organization did not cover any detection capabilities (no information was shared about that), but it is highly likely that there were none on the infected servers – otherwise, someone would notice such malicious events.
It is hard to assume which initial access technique was used since we only know that a certain server segment was infected for a while and could only spread across the network once they began their server migration. This indicates that CloudNordic did indeed have appropriate network segmentation, which was unfortunately compromised once the infected segment got connected to the internal network by mistake, leading to devastating events.
What was done right
Two things we would like to point out that CloudNordic did well (at least according to the information available):
- Implementation of backup systems.
- Applying Network Segmentation.
With the information we have, it is hard to say what backup strategy they used. They mention backups, a great preventive measure – especially effective against ransomware attacks – but it also shows that backups do not guarantee a foolproof setup.
CloudNordic’s case shows us how important network segmentation is. If those servers were not accidentally connected to the internal network, the company would (probably) not be in such a state today – but the infections would remain dormant, mitigating it by a good prevention measure (network segmentation).

NIS2: Vision, key objectives, and tactical strategies for your organization
This whitepaper provides information on the NIS2 directive, including its primary goals, scope, and the requirements imposed on companies.
What can you do to prevent such intrusions from causing damage on this scale?
We would like to truly emphasize the fact that simply deploying preventive countermeasures and ticking a ‘checkmark’ in a box, as done & completed, is not sufficient. Below, we list some of our recommendations for everyone that would help your business survive through a similar incident that CloudNordic had. We summarized only the key recommendations here, as lengthy lists are not always fruitful and quite repetitive – making it hard for CISOs to distinguish the priority ones.
1: Network Segmentation is great and needed, but by itself is not enough.
We would consult our customers (and readers) for several more techniques and mechanisms to improve that capability.
- Applying the Principle of Least Privilege and RBAC (Role-Based Access Control).
This countermeasure is no joke and probably one of the most important ones, but also one that is neglected most. By following this rule, you can limit hosts, services, users, and networks from accessing data and functions outside their immediate responsibility. This implementation provides you with a more comprehensive security posture and enables security teams to monitor easier and track traffic throughout your network. In CloudNordic’s case, we can derive from their words that they had network segmentation, but it is not clear whether they applied RBAC and Least privilege principle – based on what was described, it is unlikely, as even if infected servers were connected to the internal network, these two mechanisms would prevent whatever the infected service/user was from accessing the administration tools on the internal network (they should not have such privilege). - Audit and Monitoring.
By applying network segmentation, your organization did increase its proneness to lateral movements and infection spreading. However, this does not prevent the initial compromise in a given network segment. And you should know if your environment is compromised or not. That is why organizations should also deploy monitoring capabilities in each segment to detect potential intrusions. From what we learned in CloudNordic’s case, such capabilities were not at the disposal in the infected segment. Otherwise, they would know about the infection.
2: Invest in routine checkups.
Treat your business (thus your IT environment) as you treat your body. If you want it to remain healthy, perform routine checkups that consist of:
- Penetration Testing: Test how hard or easy it is to access your crown jewels.
- Vulnerability Assessment: Learn which holes and where they are in your environment.
- Compromise Assessment: Learn if your environment is already compromised without your awareness.
- Red Team exercises: See if you are prepared to deal with a cybersecurity incident.
- Security Advisories service based on Threat Intelligence: Learn who your adversaries are and what capabilities and techniques they use so you can improve your defenses wisely.
These checkups will help your business stay strong and protected from potential infections that could have devastating results.
3: Implement comprehensive security monitoring with threat intelligence and incident response.
This is your ultimate end goal. However, it requires a certain amount of investment and preparation, so even if you start with improving your Network and IT architecture and then applying the routine checkups, it is already a great start until you are ready for the ultimate protection. Having 24/7 capabilities to monitor your IT environment and an Incident Response team ready on standby in case of a detected breach is something that every organization that values its business should strive for. Fueled with Threat Intelligence, your security teams and Incident responders can maintain high efficiency despite the potential big workload. Since establishing such capabilities can be quite an investment, there is always an option to outsource it to a third-party team of experts to deal with this for you.
That said, cybersecurity is an ever-growing and ever-adapting field in technology. And it will remain so. This is due to a simple fact – it involves humans on both ends. No AI will change this. It will always be human motivation to breach the victim’s environment with a certain goal in mind (extortion, causing damage, causing disruption, etc.). The tools used in this process will always be dynamic, and both sides (adversaries and defenders) will always have to continue to adapt to these changes. Meaning, that there is no ‘Shopping List’ for cybersecurity that you can just take and apply and then sit down to relax. This is why we believe that organizations should partner with cybersecurity service providers to focus on growing their business while the service providers will focus on staying on top of this ever-changing field to protect your business.
About the author

David Kasabji
Principal Threat Intelligence Analyst
David Kasabji is a Principal Threat Intelligence Analyst at the Conscia Group. His main responsibility is to deliver actionable intelligence in different formats according to target audiences, ranging from Conscia’s own cyberdefense, all the way to the public media platforms. His work includes collecting, analyzing, and disseminating intelligence, reverse engineering obtained malware samples, crafting TTPs […]
Related











