Blog
Diving Deep: How to detect Typosquatting
Typosquatting is a type of social engineering attack where a threat actor registers domains with deliberately misspelled names of known brands or websites and hosts malicious content on them or lures visitors to input sensitive data into the website. This type of attack targets internet users who incorrectly type a URL into their web browser or […]

Typosquatting is a type of social engineering attack where a threat actor registers domains with deliberately misspelled names of known brands or websites and hosts malicious content on them or lures visitors to input sensitive data into the website. This type of attack targets internet users who incorrectly type a URL into their web browser or click on a URL in a phishing e-mail. To increase the chance of a successful cyber-attack, hackers will try to mimic the look of the original website.
Typosquatting is not limited only to well-known brands and websites. Any brand could be picked, and sometimes it is even easier to perform this attack on lesser-known brands as the more believable domain names will be available for registering. Typosquatting is not only a problem for users, but it also damages the brand’s and organization’s reputation, which is the target of typosquatting.
In this article, we will show you how to detect typosquatting.
Toolkit for detecting typosquatting
To detect typosquatting, we will use a tool called DNSTwist by Marcin Ulikowski. The tool is written in Python and it works by generating a large list of permutations based on a domain name you provide and then it will check if any of those permutations are in use. On the provided GitHub, you can find installation instructions. You may also inspect requirements.txt to see any requirements for the tool.
There are two options for quick installation through Python’s PIP:
pip install dnstwistpip install dnstwist[full]
The difference is that the full version will install all the requirements, while others will just install the bare minimum. You can also install the bare minimum version and install other requirements depending on your needs.
Now we need to think of what organization might be targeted by typosquatting attacks. You could use your own organization’s domain, but for this demo purposes let’s use something popular, like google.com.
Detecting potential domain abuse
We will execute the following command:
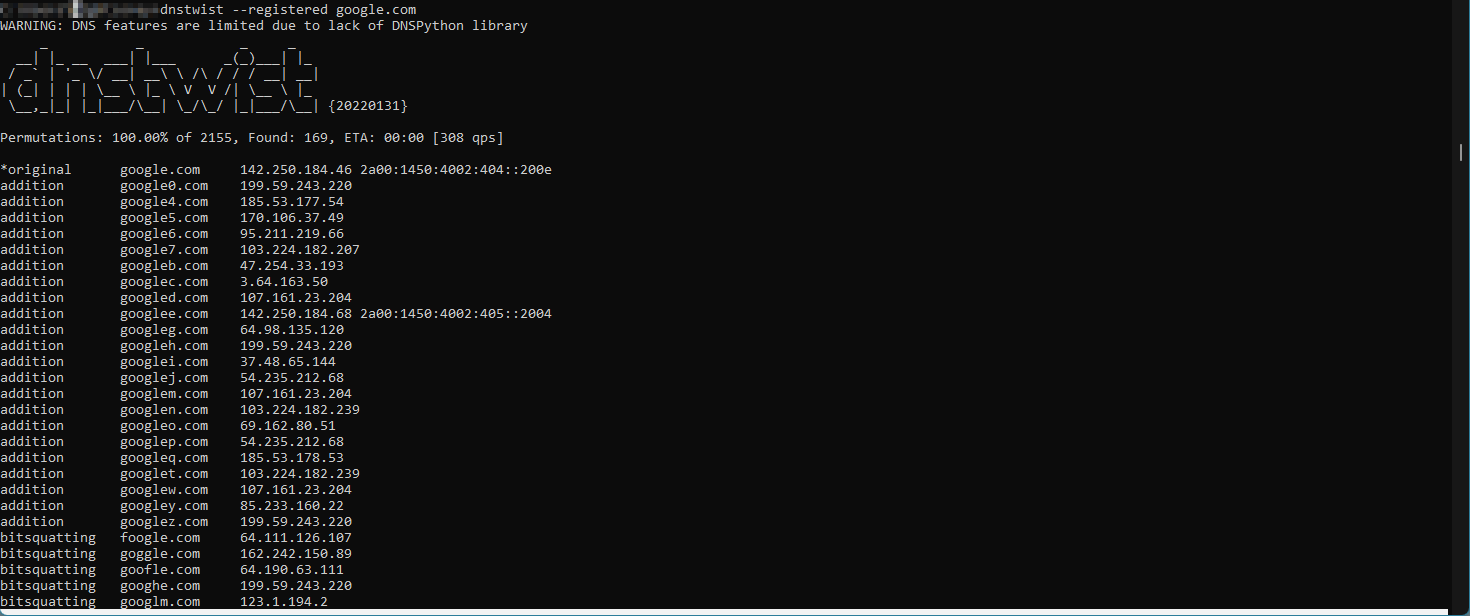
dnstwist --registered google.comWe are using an option registered in order to track only registered domains. You could also omit that, and the tool will output all the permutations to your input, even if they are not registered. That could be useful to you to track which similar domains are still available for purchase.
DNSTwist offers a lot more options that you can try out. One interesting feature is ssdeep which is able to detect similar HTML source code. For each generated domain, the tools will fetch content from the responding HTTP server, normalize HTML code and compare its fuzzy hash with the one for the original domain (your input).
If you are not keen on CLI tools, you can try the browser version, but keep in mind that it does not allow for any advanced usage.
What to do once you detect potential domain abused by typosquatting
Since Google is a popular brand and website, we received a lot of results. If we assume that you are Google and you find on this list a registered domain, such as goog1e.com and you can verify that it is not registered by yourself – this is then a potential suspect for typosquatting or domain abuse.
In such case, you would request a domain takedown. Domain takedown is a process of removing infringing domains from the internet. This is usually done on registrar level, but sometimes these might be slow or unresponsive.
At Conscia ThreatInsights we use a modified version of DNSTwist to detect potential domain abuse and if we confirm one, we can request a domain takedown on behalf of our clients.

NIS2: Vision, key objectives, and tactical strategies for your organization
This whitepaper provides information on the NIS2 directive, including its primary goals, scope, and the requirements imposed on companies.
About the author

David Kasabji
Principal Threat Intelligence Analyst
David Kasabji is a Principal Threat Intelligence Analyst at the Conscia Group. His main responsibility is to deliver actionable intelligence in different formats according to target audiences, ranging from Conscia’s own cyberdefense, all the way to the public media platforms. His work includes collecting, analyzing, and disseminating intelligence, reverse engineering obtained malware samples, crafting TTPs […]
Related











