Operational Technology (OT) Security
Industrial control systems and industry IoT solutions fall easy prey to both trivial and sophisticated attacks. We provide solutions that focus on industrial defense smartly – using detection/response approaches that best fit these environments.
The security of industrial control systems (ICS) and industry IoT solutions has never been more important.
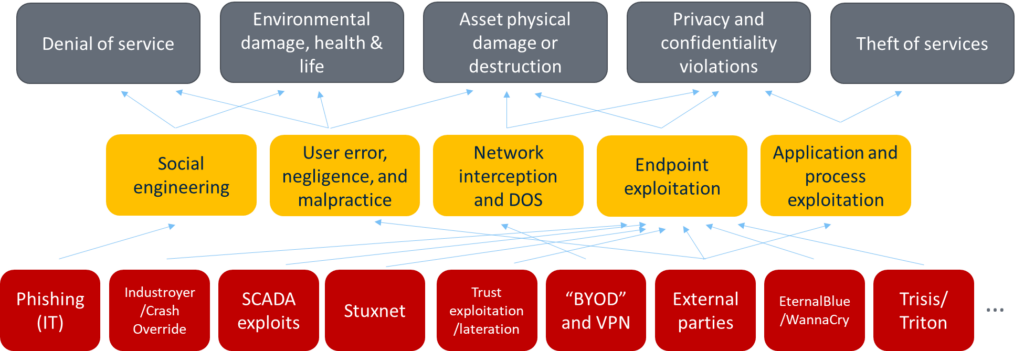
High-profile attacks against critical infrastructure could result in a loss of critical services, environmental damage, and even loss of life. And because these digital systems interact with the physical world, the risks cross the digital barrier into reality.
ICS systems have traditionally relied on isolation and obscurity to mitigate the risk of digital attacks. But with increasing connectivity between classic IT and operational technology (OT), this isolation is gradually disappearing. In addition, obscurity is no longer a viable defense due to standardization and vulnerability research.

Why choose Conscia?
Conscia creates OT security solutions for specific environments, offering you:
- Experience: Creating enterprise and service provider security solutions for over 20 years.
- Speed: Engaging quickly using our pre-defined practices.
- Cost effective services: Offering managed OT/ICS SOC services that are significantly more cost-effective than comparable in-house solutions.
Solution Description:
Traditionally, risk management uses historically successful IT preventive controls, such as hardening, patching, SDLC, active vulnerability assessment, and tight access control. However, this is no longer enough in the OT/ICS world. Processes and people are used to operating mission-critical systems with only safety in mind, change management runs at a different pace, and trust between components is the norm. To secure the complex systems of today, a different approach is needed.
To address the problem, Conscia acts as detective and observes OT/ICS systems in real-time, quickly responding to any suspicious or anomalous behavior. This provides the following benefits:
- Fast detection of intruders and malicious code (minutes to hours), enabling extremely quick response processes to limit damage and business loss. For comparison, attackers spent 6 months examining the target ICS in the 2015 Ukraine power distribution attacks.
- No change and no interference with existing OT applications and processes, to ensure uninterrupted operations using today’s technology.
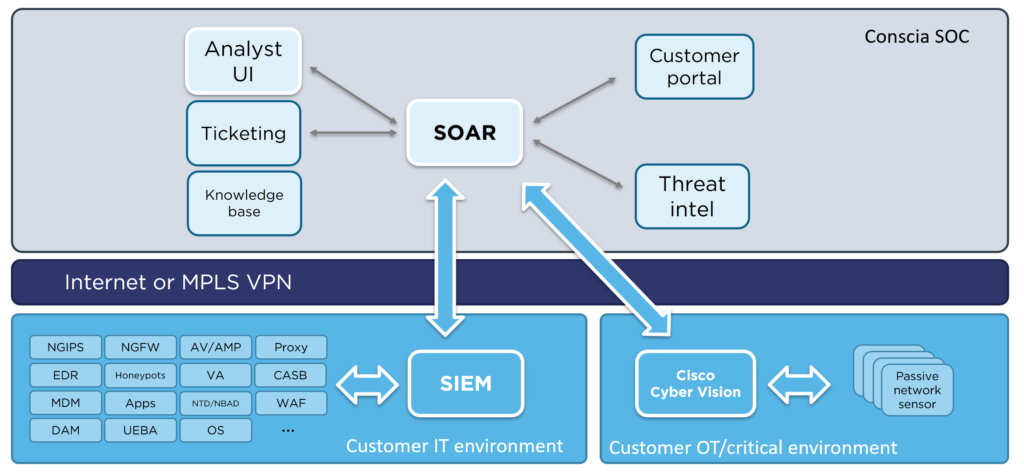
Our solution is based on OT network data capture and anomaly-based analysis and detection, using completely passive network sensors at the customer site. By creating baselines of known good system behavior, we can detect suspicious or malicious deviations and known, specific attacks against the system.
Our solution can be operated by your business or managed by Conscia’s Security Operations Center (SOC). Our analysts are trained in ICS/OT risks and vulnerabilities and react to alerts with the help of extensive automation.
Our cybersecurity solutions
Navigate through our cybersecurity solution framework below to read more about our solutions and services.